Rilasci e aggiornamenti
Tutte le ultime Vectra AI e miglioramenti apportati Vectra AI .
Grazie! La tua richiesta è stata ricevuta!
Ops! Si è verificato un errore durante l'invio del modulo.
Chiaro
Data:
Gennaio 2026
Rilascio:
2026.1
RUX: Fornitura SaaS
Copertura
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- Vectra AI la transizione dei rilevamenti precedentemente forniti tramite il motore Suricata verso rilevamenti nativi eseguiti direttamente sul motore di flusso Vectra. Questo impegno costante garantisce a tutti i clienti una copertura avanzata dei comportamenti degli aggressori, senza richiedere l'attività di protocollo sospetto (SPA) o affidarsi alla logica di rilevamento basata su firme.
- Questa versione introduce ulteriori rilevamenti per Cobalt Strike, Brute Ratel e PowerShell Empire.
- Vectra AI migliorato la precisione del rilevamento Smash and Grab assicurando che i nomi di dominio di destinazione vengano aggiornati correttamente quando vengono osservati più tardi in una sessione. Questo miglioramento consente alla logica della whitelist di funzionare come previsto, riducendo gli avvisi non necessari e migliorando l'affidabilità dei rilevamenti Smash and Grab.
- Vectra AI migliorato i rilevamenti a livello di informazioni per gli strumenti di gestione e monitoraggio remoto (RMM) inserendo correttamente i dettagli del protocollo dell'applicazione nei metadati di rilevamento. Questo miglioramento fornisce un contesto più chiaro sulle pagine Host quando viene osservata un'attività RMM, migliorando la chiarezza investigativa e mantenendo al contempo un'esperienza di allerta a basso rumore e senza punteggio.
- Vectra AI perfezionato la logica del suo di rilevamento Mythic C2 per ridurre i falsi positivi, rendendo più rigorosa la valutazione dei campi dei certificati dei server. Questo aggiornamento restringe la corrispondenza dei modelli eccessivamente ampi, impedendo che domini benigni contenenti termini simili attivino avvisi e migliorando la fedeltà complessiva del rilevamento.
Nuovo rilevamento: operazione sospetta Azure - Modifica della politica di sicurezza DNS
Vectra AI introdotto un nuovo rilevamento che mette in evidenza comportamenti sospetti associati alle modifiche della registrazione del flusso di rete. Il nuovo rilevamento Azure Suspect Operation - DNS Security Policy Modification è progettato per mettere in evidenza le azioni in cui è stato osservato che un'entità ha eliminato o modificato una risorsa associata a una politica di sicurezza DNS. Ciò potrebbe disabilitare la registrazione delle query DNS o alterare in altro modo la risoluzione DNS all'interno dell'ambiente Azure. Gli autori delle minacce utilizzano questa tecnica per compromettere la registrazione ed eludere il rilevamento.
Nuovo rilevamento: operazione sospetta Azure - Registri flusso disabilitati
Vectra AI introdotto un nuovo rilevamento che evidenzia comportamenti sospetti associati alle modifiche della registrazione del flusso di rete. Il nuovo rilevamento Azure Suspect Operation - Flow Logs Disabled è progettato per evidenziare le azioni in cui è stato osservato che un'entità ha eliminato una risorsa di registrazione del flusso Azure. Ciò indica la rimozione della registrazione del flusso per una rete virtuale, una sottorete o una scheda NIC ed è una tecnica di elusione cloud ben nota sfruttata dagli aggressori per compromettere la visibilità e la verificabilità delle azioni.
Nuovo rilevamento: operazione sospetta Azure - Modifica della configurazione della sicurezza di rete
Vectra AI introdotto una nuova funzionalità di rilevamento che individua comportamenti sospetti associati a modifiche delle configurazioni di sicurezza della rete. La nuova funzionalità Azure Suspect Operation - Network Security Config Change è progettata per individuare azioni in cui un'entità crea o modifica in modo imprevisto un gruppo di sicurezza di rete Azure (NSG) o modifica una risorsa firewall Azure. Ciò potrebbe indicare un movimento laterale all'interno della rete o un tentativo di compromettere le difese.
Nuovo rilevamento: operazione sospetta su Azure - Eliminazione rischiosa
Vectra AI introdotto un nuovo sistema di rilevamento che individua comportamenti sospetti associati a cancellazioni ad alto rischio in un ambiente Azure. Il nuovo sistema di rilevamento Azure Suspect Operation - Risky Deletion è progettato per individuare azioni quali la rimozione di backup sensibili e politiche di immutabilità che gli autori delle minacce potrebbero utilizzare per eludere le difese e causare danni. Questo sistema di rilevamento rafforza la copertura contro gli autori cloud come Storm-0501 che hanno sfruttato queste tecniche in attacchi documentati.
Miglioramento del rilevamento: attività TOR Azure
Sono stati introdotti miglioramenti al modello di rilevamento delle attività TOR di Azure per ottimizzare la prioritizzazione delle entità associate a questo comportamento. In futuro, Vectra AI maggiore risalto alle entità che mostrano questo comportamento, in modo che vengano visualizzate tempestivamente nella pagina Rispondi. A seguito di questa modifica, i clienti potrebbero osservare un leggero aumento delle entità prioritarie.
Nuovo rilevamento: operazione sospetta in Azure AD: aggiunto utente ospite
Vectra AI introdotto un nuovo rilevamento che mette in evidenza comportamenti sospetti associati all'accesso iniziale. Il nuovo rilevamento Azure AD Suspect Operation: Guese User Added è progettato per mettere in evidenza comportamenti in cui si osserva che un soggetto invita un utente ospite esterno nell'ambiente, il che è incoerente con il profilo comportamentale osservato del soggetto. Questo metodo viene utilizzato dagli autori delle minacce in una campagna di ingegneria sociale per stabilire l'accesso e mantenere la persistenza nell'ambiente della vittima.
Nuovo rilevamento: operazione sospetta di Azure AD: accesso insolito da un proxy
Vectra AI introdotto un nuovo sistema di rilevamento che individua comportamenti sospetti associati all'accesso iniziale. Il nuovo sistema di rilevamento Azure AD Suspect Operation: Unusual Sign-On from a Proxy è progettato per individuare azioni in cui si osserva che un soggetto effettua l'accesso utilizzando un proxy o una VPN in modo non coerente con il suo comportamento normale. Si tratta di un metodo utilizzato dagli autori delle minacce per mascherare la loro vera posizione. Questo rilevamento è il primo a sfruttare il nuovo motore Threat Intelligence Vectra AI, una raccolta di feed di minacce privati e con licenza progettati per fornire ricche informazioni contestuali e reputazionali per la massima chiarezza possibile dei segnali.
Migliorata visibilità della crittografia Kerberos
Abbiamo migliorato il modo in cui vengono riportati i metadati di crittografia Kerberos per fornire una visibilità più accurata delle attività di autenticazione.
La piattaforma ora distingue chiaramente tra:
- I codici di crittografia richiesti dal cliente
- Il codice utilizzato per proteggere la chiave di sessione Kerberos
- Il codice utilizzato per crittografare il ticket Kerberos
Questo miglioramento rafforza l'indagine sulle tecniche di attacco basate su Kerberos, tra cui AS-REP Roasting e Kerberoasting, garantendo che venga visualizzato il contesto di crittografia corretto per ogni fase di autenticazione.
I team di sicurezza che eseguono la ricerca delle minacce o esaminano la telemetria di autenticazione potrebbero notare campi di cifratura Kerberos aggiornati a partire dalla fine di gennaio. Non è richiesta alcuna azione, ma è necessario rivedere le query o i flussi di lavoro esistenti per tenere conto dei metadati aggiornati.
Maggiore visibilità della pre-autenticazione Kerberos
Abbiamo introdotto una maggiore visibilità negli scambi di pre-autenticazione Kerberos (PA-DATA) durante i flussi AS-REQ e AS-REP.
La piattaforma ora espone sia i tipi che i conteggi dei dati di pre-autenticazione utilizzati dal client e restituiti dal KDC. Ciò fornisce un contesto aggiuntivo per comprendere come viene negoziata l'autenticazione Kerberos e aiuta i team di sicurezza a identificare comportamenti di pre-autenticazione anomali o imprevisti.
Questi miglioramenti consentono un'analisi più efficace degli attacchi basati su Kerberos e delle configurazioni errate, in particolare quelli che coinvolgono meccanismi di pre-autenticazione modificati o aggirati.
I cacciatori di minacce e gli analisti che esaminano la telemetria dell'autenticazione Kerberos potrebbero osservare nuovi metadati di pre-autenticazione a partire dalla fine di gennaio.
Data:
Gennaio 2026
Rilascio:
9.8
QUX: Interfaccia apparecchiature
Copertura
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- Vectra AI la transizione dei rilevamenti precedentemente forniti tramite il motore Suricata verso rilevamenti nativi eseguiti direttamente sul motore di flusso Vectra. Questo impegno costante garantisce a tutti i clienti una copertura avanzata dei comportamenti degli aggressori, senza richiedere l'attività di protocollo sospetto (SPA) o affidarsi alla logica di rilevamento basata sulle firme.
Questa versione introduce ulteriori rilevamenti per Cobalt Strike, Brute Ratel e PowerShell Empire. - Vectra AI migliorato la precisione del rilevamento Smash and Grab assicurando che i nomi di dominio di destinazione vengano aggiornati correttamente quando vengono osservati più tardi in una sessione. Questo miglioramento consente alla logica della whitelist di funzionare come previsto, riducendo gli avvisi non necessari e migliorando l'affidabilità dei rilevamenti Smash and Grab.
- Vectra AI migliorato i rilevamenti a livello di informazioni per gli strumenti di gestione e monitoraggio remoto (RMM) inserendo correttamente i dettagli del protocollo dell'applicazione nei metadati di rilevamento. Questo miglioramento fornisce un contesto più chiaro sulle pagine Host quando viene osservata un'attività RMM, migliorando la chiarezza investigativa e mantenendo al contempo un'esperienza di allerta a basso rumore e senza punteggio.
- Vectra AI perfezionato la logica di rilevamento Mythic C2 per ridurre i falsi positivi, rendendo più rigorosa la valutazione dei campi dei certificati server. Questo aggiornamento restringe la corrispondenza dei modelli eccessivamente ampia, impedendo che domini benigni contenenti termini simili attivino avvisi e migliorando la fedeltà complessiva del rilevamento.
Nuovo rilevamento: operazione sospetta Azure - Modifica della politica di sicurezza DNS
Vectra AI introdotto un nuovo rilevamento che mette in evidenza comportamenti sospetti associati alle modifiche della registrazione del flusso di rete. Il nuovo rilevamento Azure Suspect Operation - DNS Security Policy Modification è progettato per mettere in evidenza le azioni in cui è stato osservato che un'entità ha eliminato o modificato una risorsa associata a una politica di sicurezza DNS. Ciò potrebbe disabilitare la registrazione delle query DNS o alterare in altro modo la risoluzione DNS all'interno dell'ambiente Azure. Gli autori delle minacce utilizzano questa tecnica per compromettere la registrazione ed eludere il rilevamento.
Nuovo rilevamento: operazione sospetta Azure - Registri flusso disabilitati
Vectra AI introdotto un nuovo rilevamento che evidenzia comportamenti sospetti associati alle modifiche della registrazione del flusso di rete. Il nuovo rilevamento Azure Suspect Operation - Flow Logs Disabled è progettato per evidenziare le azioni in cui è stato osservato che un'entità ha eliminato una risorsa di registrazione del flusso Azure. Ciò indica la rimozione della registrazione del flusso per una rete virtuale, una sottorete o una scheda NIC ed è una tecnica di elusione cloud ben nota sfruttata dagli aggressori per compromettere la visibilità e la verificabilità delle azioni.
Nuovo rilevamento: operazione sospetta Azure - Modifica della configurazione della sicurezza di rete
Vectra AI introdotto una nuova funzionalità di rilevamento che individua comportamenti sospetti associati a modifiche delle configurazioni di sicurezza della rete. La nuova funzionalità Azure Suspect Operation - Network Security Config Change è progettata per individuare azioni in cui un'entità crea o modifica in modo imprevisto un gruppo di sicurezza di rete Azure (NSG) o modifica una risorsa firewall Azure. Ciò potrebbe indicare un movimento laterale all'interno della rete o un tentativo di compromettere le difese.
Nuovo rilevamento: operazione sospetta Azure - Eliminazione ad alto rischio
Vectra AI introdotto un nuovo sistema di rilevamento che individua comportamenti sospetti associati a cancellazioni ad alto rischio in un ambiente Azure. Il nuovo sistema di rilevamento Azure Suspect Operation - High-Risk Deletion è progettato per individuare azioni quali la rimozione di backup sensibili e politiche di immutabilità che gli autori delle minacce potrebbero utilizzare per eludere le difese e causare danni. Questo sistema di rilevamento rafforza la copertura contro gli autori cloud come Storm-0501 che hanno sfruttato queste tecniche in attacchi documentati.
Miglioramento del rilevamento: attività TOR Azure
Sono stati introdotti miglioramenti al modello di rilevamento delle attività TOR di Azure per ottimizzare la prioritizzazione delle entità associate a questo comportamento. In futuro, Vectra AI maggiore risalto alle entità che mostrano questo comportamento, in modo che vengano visualizzate tempestivamente nella pagina Rispondi. A seguito di questa modifica, i clienti potrebbero osservare un leggero aumento delle entità prioritarie.
Nuovo rilevamento: operazione sospetta in Azure AD: aggiunto utente ospite
Vectra AI introdotto un nuovo rilevamento che mette in evidenza comportamenti sospetti associati all'accesso iniziale. Il nuovo rilevamento Azure AD Suspect Operation: Guest User Added è progettato per mettere in evidenza comportamenti in cui si osserva che un soggetto invita un utente ospite esterno nell'ambiente, il che è incoerente con il profilo comportamentale osservato del soggetto. Questo metodo viene utilizzato dagli autori delle minacce in una campagna di ingegneria sociale per stabilire l'accesso e mantenere la persistenza nell'ambiente della vittima.
Nuovo rilevamento: operazione sospetta di Azure AD: accesso insolito da un proxy
Vectra AI introdotto un nuovo sistema di rilevamento che individua comportamenti sospetti associati all'accesso iniziale. Il nuovo sistema di rilevamento Azure AD Suspect Operation: Unusual Sign-On from a Proxy è progettato per individuare azioni in cui si osserva che un soggetto effettua l'accesso utilizzando un proxy o una VPN in modo non coerente con il suo comportamento normale. Si tratta di un metodo utilizzato dagli autori delle minacce per mascherare la loro vera posizione. Questo rilevamento è il primo a sfruttare il nuovo motore Threat Intelligence Vectra AI, una raccolta di feed di minacce privati e con licenza progettati per fornire ricche informazioni contestuali e reputazionali per la massima chiarezza possibile dei segnali.
Controllo
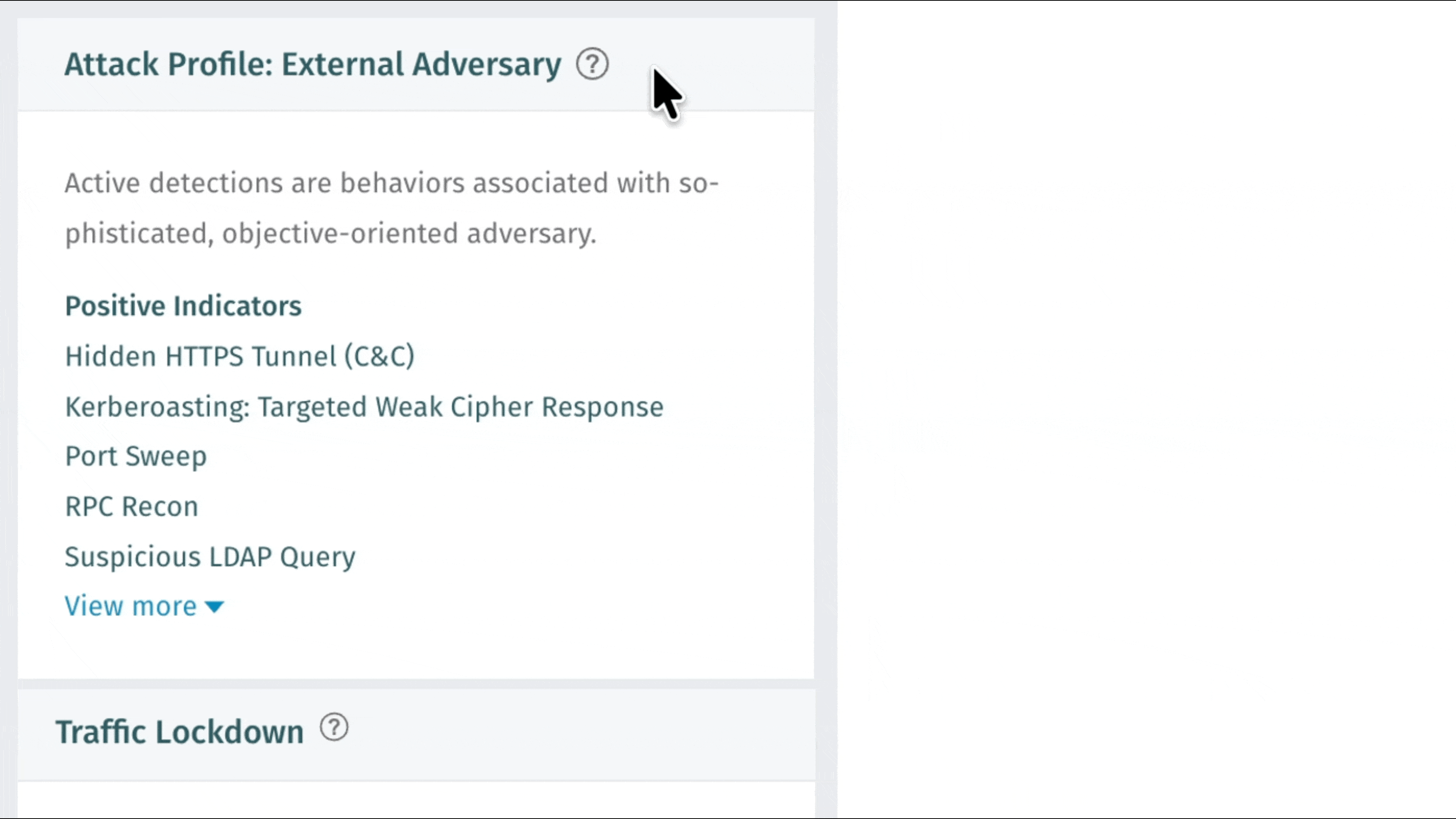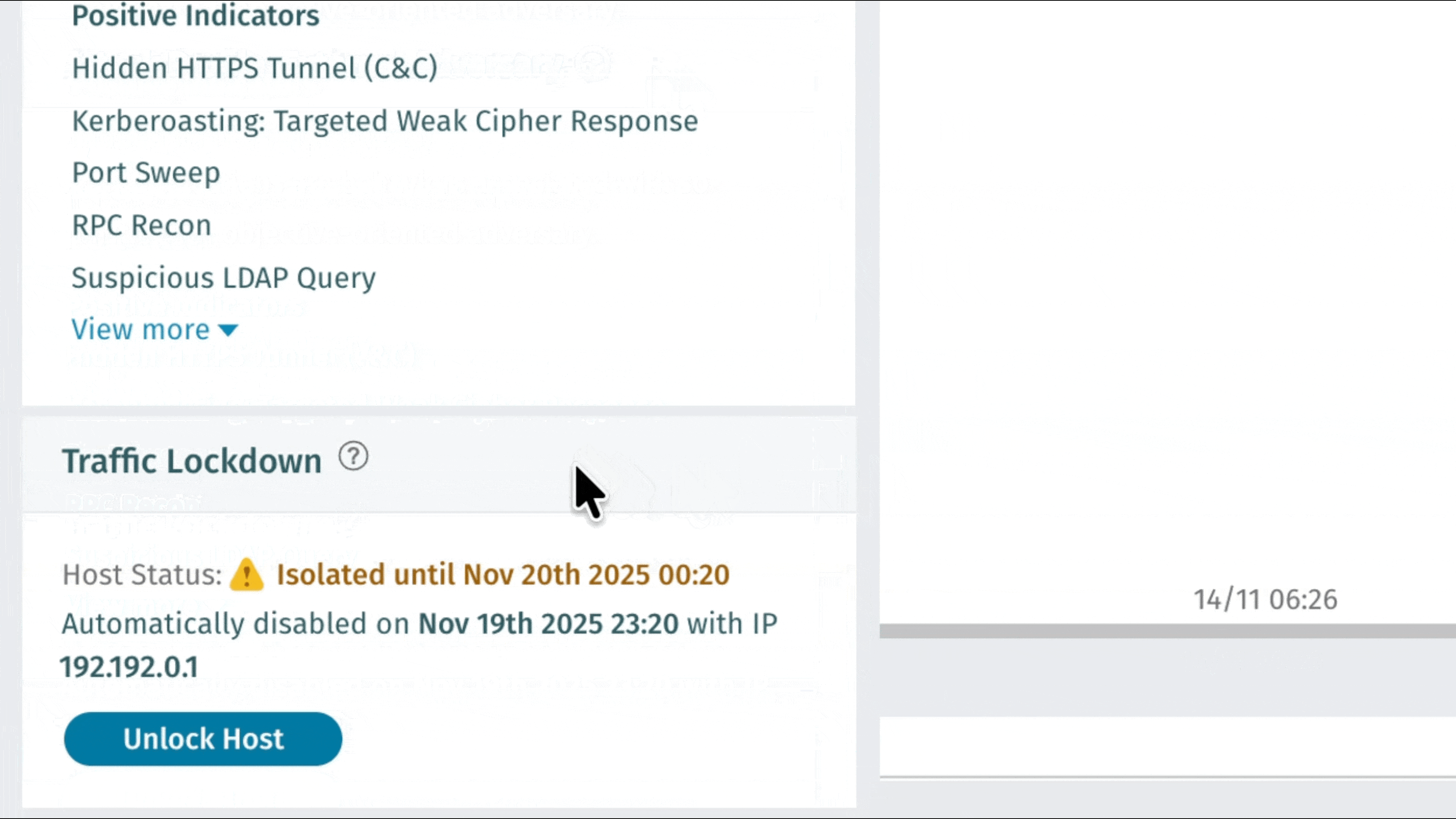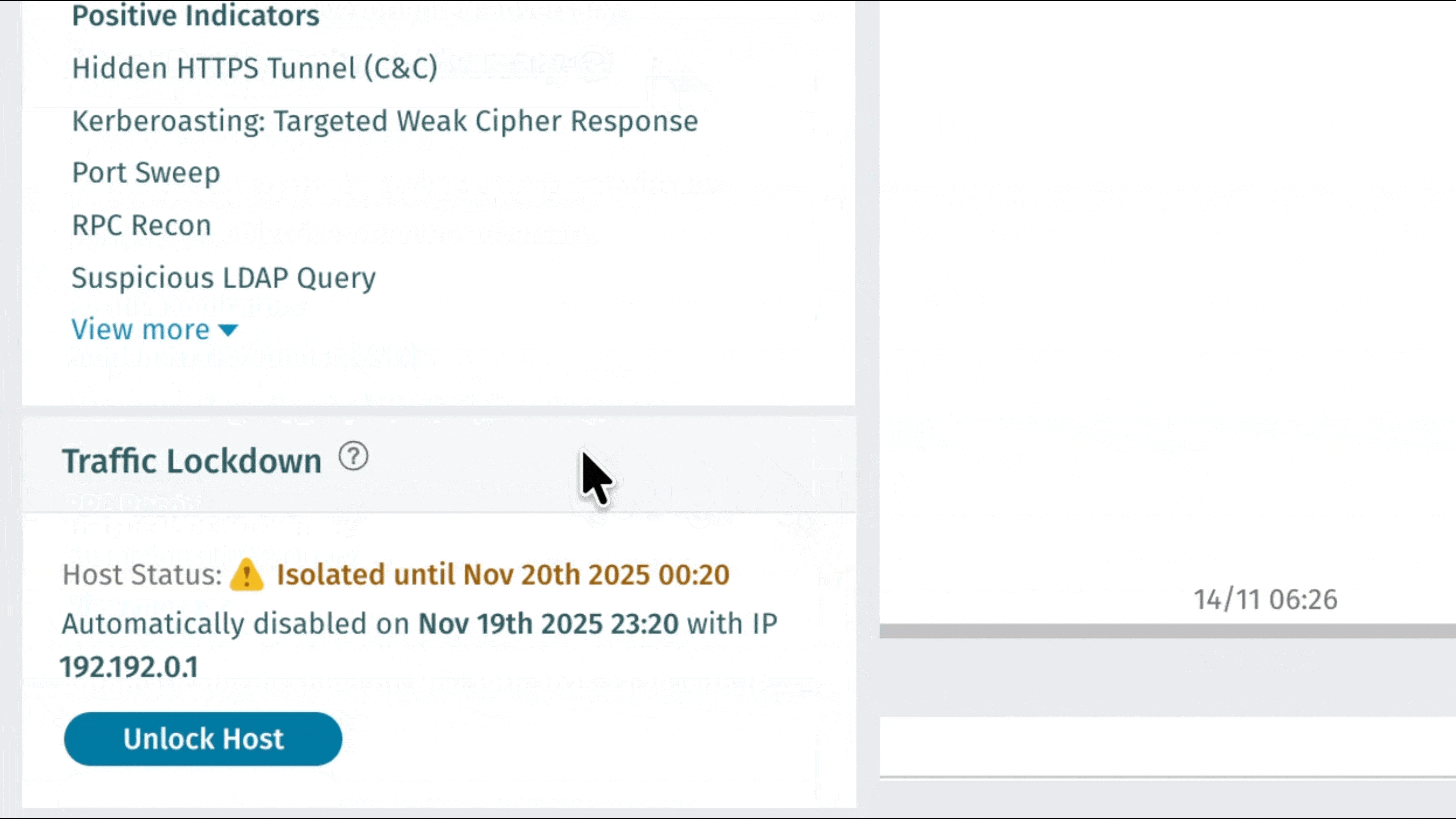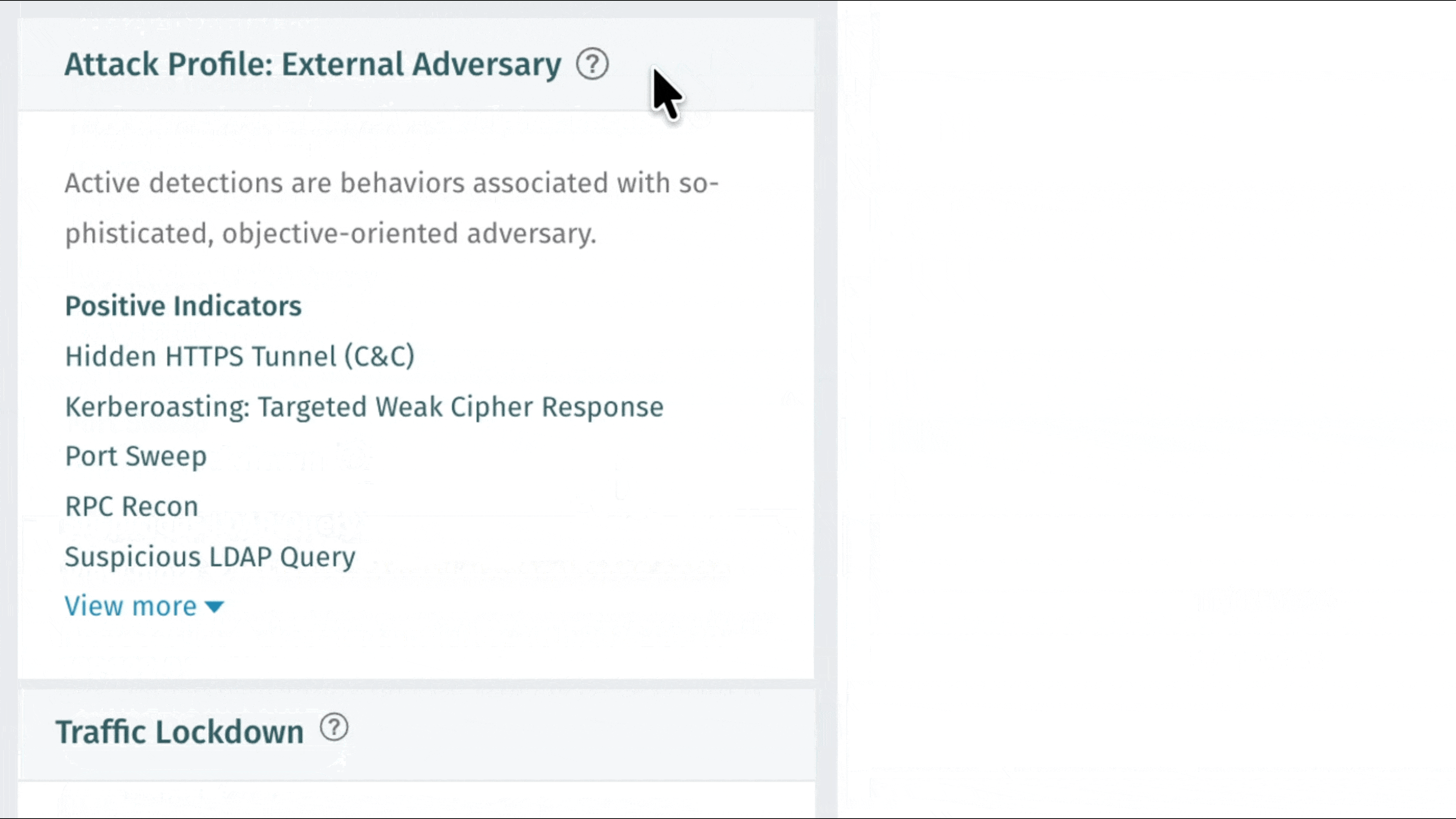
Blocco del traffico: difesa automatizzata della rete tramite integrazione firewall
Vectra AI consente ai clienti di intervenire immediatamente sulle minacce rilevate con Traffic Lockdown, una nuova funzionalità che blocca automaticamente gli host dannosi a livello di firewall. Integrandosi direttamente con i firewall supportati, Vectra AI pubblica Vectra AI gli IP delle minacce per un'applicazione immediata senza necessità di regole manuali o configurazioni complesse. I team di sicurezza ottengono un contenimento più rapido, flussi di lavoro più puliti e una protezione più forte dove conta di più: ai margini della rete. Visitate Traffic Lockdown per le istruzioni di configurazione. Per ulteriori informazioni, guardate questo podcast:
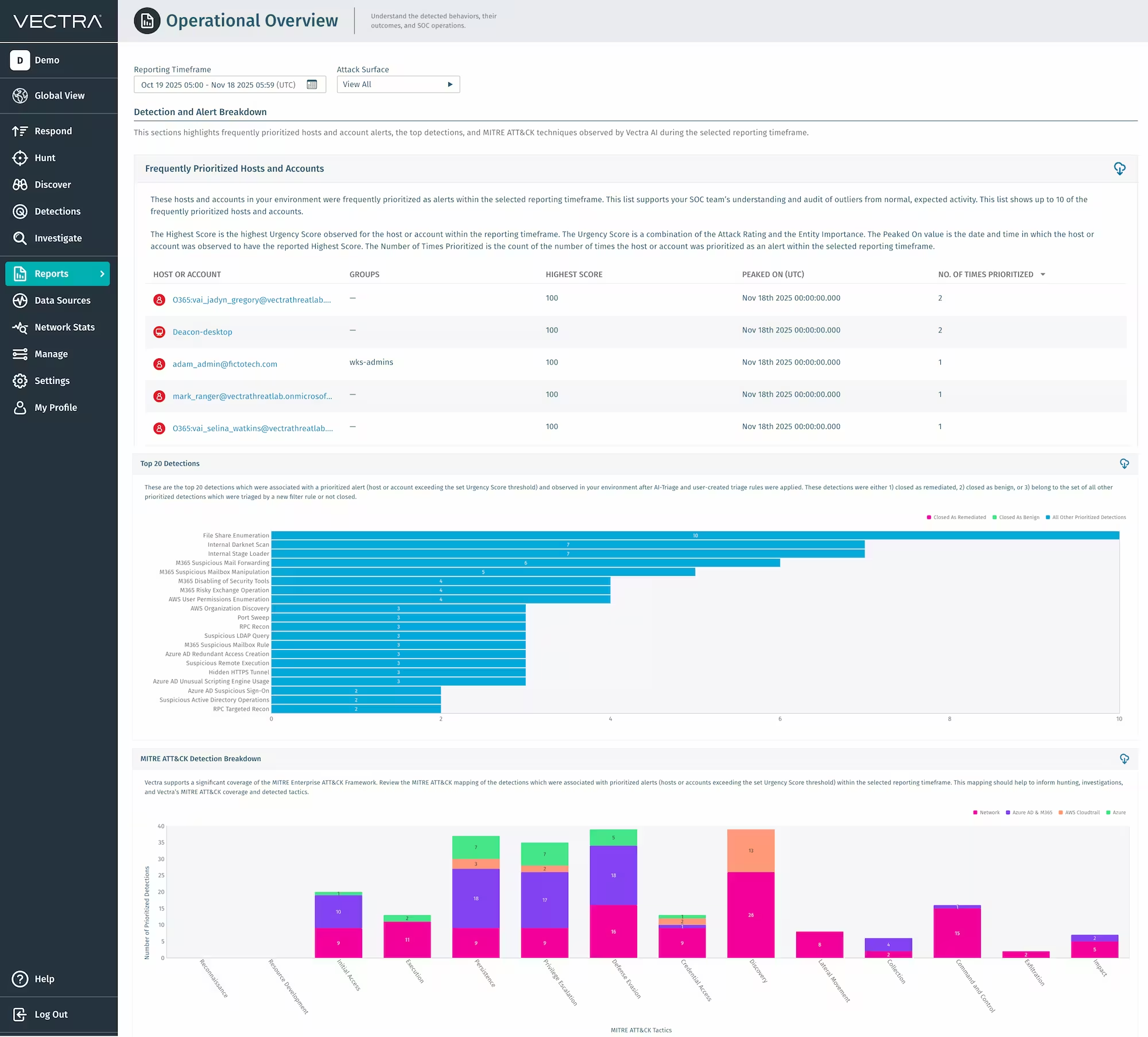
Relazione sulla panoramica operativa
Vi presentiamo il rapporto panoramica operativa, la nuova vista di comando del vostro SOC per le prestazioni e l'impatto. Questo rapporto riunisce metriche chiave come il tempo medio di assegnazione, il tempo medio di indagine e il tempo medio di risoluzione, insieme alle principali rilevazioni, MITRE ATT&CK e alle entità prioritarie in un unico dashboard chiaro e visivo. Quantifica il modo in cui Vectra AI indagini più rapide, una selezione più accurata e guadagni di efficienza misurabili. Grazie a potenti approfondimenti per le revisioni aziendali, i report esecutivi e le operazioni quotidiane, trasforma i dati sulle prestazioni in una prova di valore. Per ulteriori informazioni, guarda questo podcast:
Architettura/Amministrazione
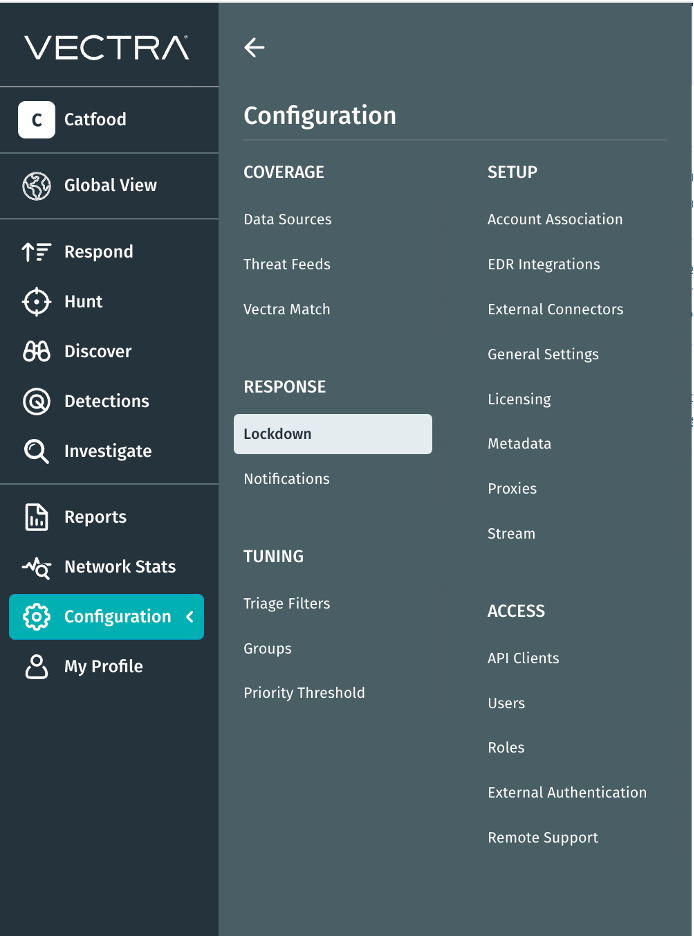
Modifica della navigazione: Configurazione
Abbiamo semplificato la gestione dell'ambiente nella Vectra AI . La nuova scheda Configurazione unifica le opzioni Gestisci e Impostazioni per riunire tutte le impostazioni di configurazione e controllo in un'unica vista chiara e intuitiva, in modo da poter trovare più rapidamente ciò che serve e agire con sicurezza. Questo aggiornamento elimina gli attriti e semplifica la navigazione. Meno ricerche. Più risultati.
Convalida certificato Syslog
Vectra 9.8 aggiunge il supporto per la convalida dei certificati server per le destinazioni Syslog che utilizzano TLS. La convalida è controllata da una casella di controllo nella configurazione Syslog, che consente ai clienti di confermare i propri certificati prima di abilitare la convalida. Seguire i passaggi di configurazione riportati nella Guida Syslog di Vectra per assistenza.
Nota: durante questo aggiornamento, abbiamo anche individuato un problema precedente che poteva causare la mancanza del certificato CA del server in determinate configurazioni. I clienti devono controllare le impostazioni Syslog in Configurazione > Risposta > Notifiche per verificare che tutti i certificati richiesti siano presenti.
Accesso SSH agli apparecchi Vectra (anteprima privata)
Vectra AI semplificato e chiarito le modalità di accesso degli amministratori alle appliance tramite SSH. Ora gli utenti autorizzati dell'interfaccia utente possono effettuare il login utilizzando le proprie credenziali SSH, anziché affidarsi a quelle condivise. vectra account. Gli amministratori possono gestire le chiavi SSH personali e le password CLI direttamente dall'interfaccia utente web. Questi aggiornamenti rendono più facile per i team seguire le best practice, ridurre la dipendenza dalle credenziali predefinite e mantenere un accesso amministrativo sicuro. Per ulteriori informazioni, visitare Guida alla documentazione per l'accesso SSH ai dispositivi Vectra.
Transizione delle distribuzioni GCP a Infrastructure Manager
Le implementazioni GCP ora utilizzano Infrastructure Manager, che sostituisce Deployment Manager, garantendo un supporto continuo e un'esperienza di implementazione più affidabile. Questo aggiornamento semplifica il modo in cui i cervelli e i sensori Vectra vengono implementati su GCP, sostituendo gli strumenti obsoleti con un approccio moderno e standardizzato.
- Le guide all'implementazione saranno aggiornate questa settimana con il processo Infrastructure Manager: Guida all'implementazione di GCP vSensor, Guida all'implementazione di GCP Brain, GuidaStream
Presentazione del sistema Vectra S127
Siamo lieti di annunciare l'ultimo arrivato nella famiglia di dispositivi Vectra: l'S127, disponibile per l'ordine da oggi! L'S127 è il successore diretto della nostra piattaforma S101, garantendo le stesse prestazioni affidabili con hardware modernizzato e spazio per crescere. L'S127 supporta una capacità sensore aggregata di 58 Gbps e prestazioni di 30 Gbps con Match . Per ulteriori informazioni sulle specifiche dell'appliance, consultare le Specifiche dell'appliance e del sensore.
- Per la guida all'implementazione, consultare la Guida rapida S127.
Data:
Dicembre 2025
Rilascio:
2025.12
RUX: Fornitura SaaS
Copertura
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- Vectra AI la transizione dei rilevamenti precedentemente forniti tramite il motore Suricata verso rilevamenti nativi eseguiti direttamente sul motore di flusso Vectra. Questo impegno costante garantisce a tutti i clienti una copertura avanzata dei comportamenti degli aggressori, senza richiedere l'attività di protocollo sospetto (SPA) o affidarsi alla logica di rilevamento basata sulle firme.
Questa versione introduce ulteriori rilevamenti per Cobalt Strike, Brute Ratel e PowerShell Empire. - Vectra AI migliorato la precisione del rilevamento Smash and Grab assicurando che i nomi di dominio di destinazione vengano aggiornati correttamente quando vengono osservati più tardi in una sessione. Questo miglioramento consente alla logica della whitelist di funzionare come previsto, riducendo gli avvisi non necessari e migliorando l'affidabilità dei rilevamenti Smash and Grab.
- Vectra AI migliorato i rilevamenti a livello di informazioni per gli strumenti di gestione e monitoraggio remoto (RMM) inserendo correttamente i dettagli del protocollo dell'applicazione nei metadati di rilevamento. Questo miglioramento fornisce un contesto più chiaro sulle pagine Host quando viene osservata un'attività RMM, migliorando la chiarezza investigativa e mantenendo al contempo un'esperienza di allerta a basso rumore e senza punteggio.
- Vectra AI perfezionato la logica di rilevamento Mythic C2 per ridurre i falsi positivi, rendendo più rigorosa la valutazione dei campi dei certificati server. Questo aggiornamento restringe la corrispondenza dei modelli eccessivamente ampia, impedendo che domini benigni contenenti termini simili attivino avvisi e migliorando la fedeltà complessiva del rilevamento.
Chiarezza
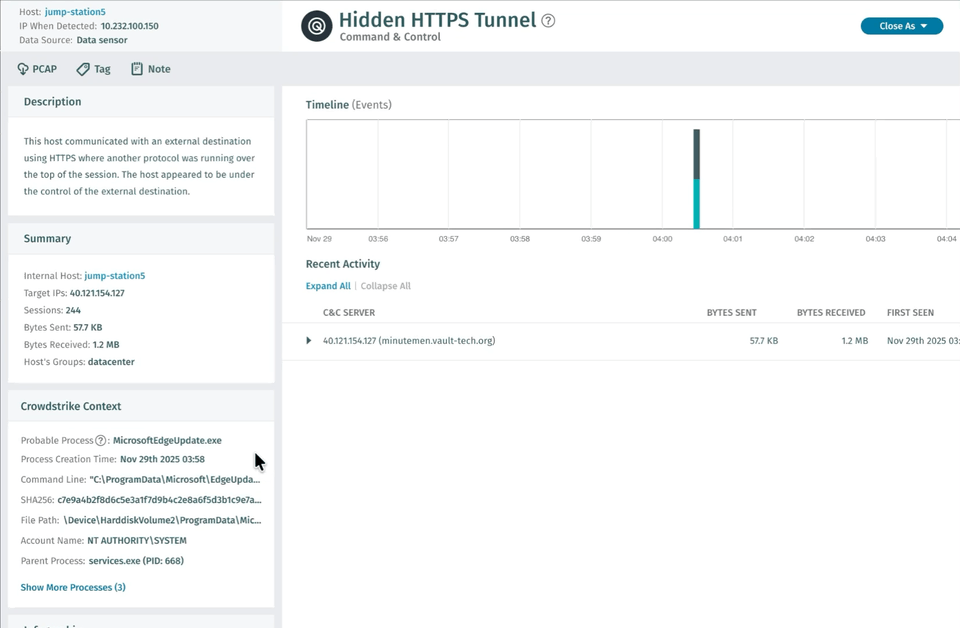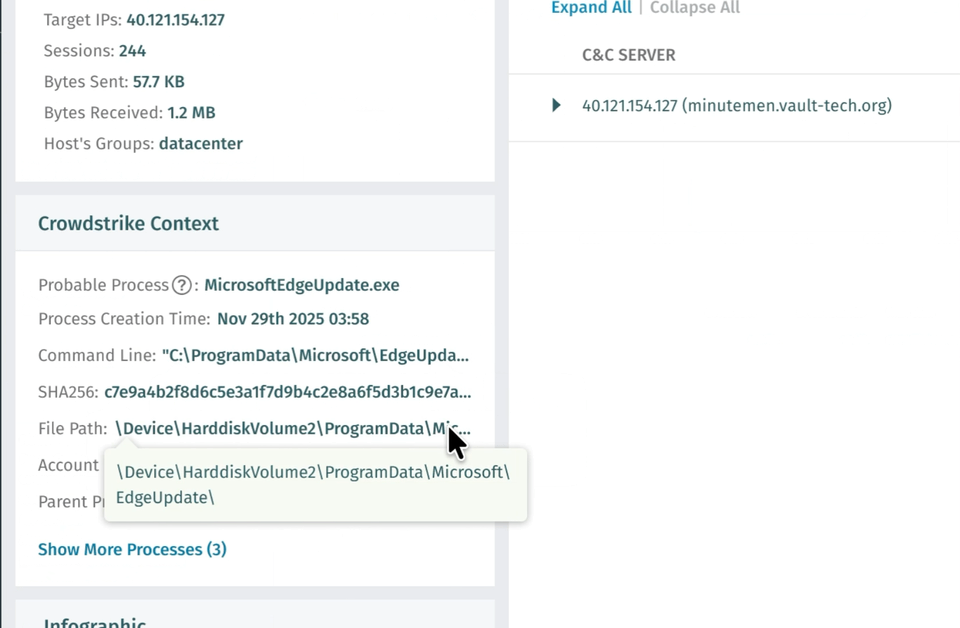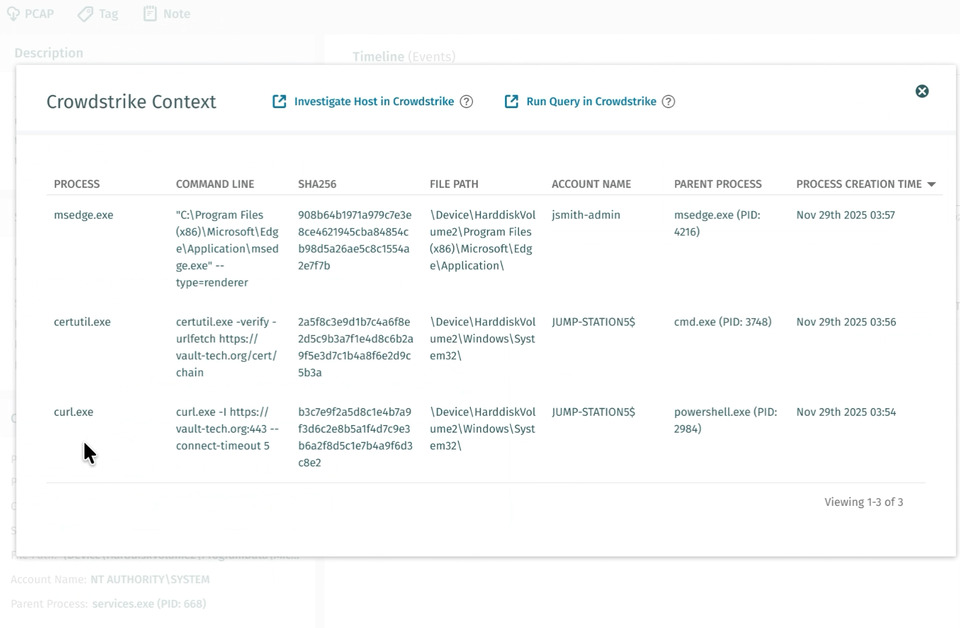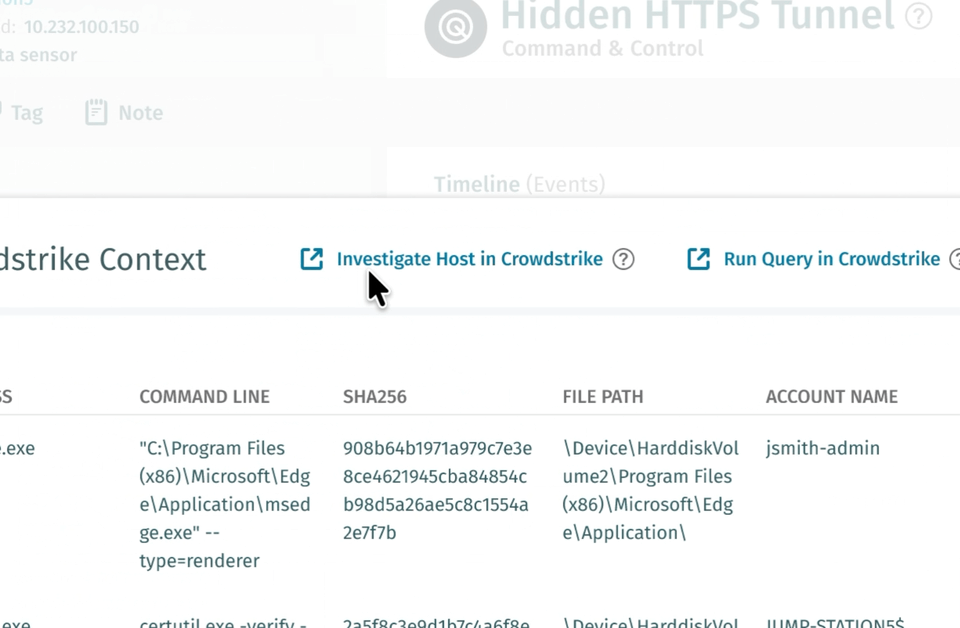
Correlazione dei processi EDR (anteprima privata)
Vectra AI rilasciato la correlazione dei processi EDR di CrowdStrike per i clienti in anteprima privata. Questa funzionalità semplifica le indagini individuando automaticamente il processo probabile correlato a un rilevamento NDR e presentandolo insieme al rilevamento nella piattaforma e quando l'evento viene raccolto tramite API.
Il risultato è un rilevamento e una risposta più efficaci, meno lavoro manuale e risultati migliori per i team di sicurezza. Elimina la necessità di una logica di correlazione SIEM o SOAR personalizzata e può far risparmiare fino a 30 minuti per ogni rilevamento. Qual era il processo che guidava C2, un browser o uno script PowerShell? È previsto o si distingue? Queste sono domande a cui gli analisti devono rispondere immediatamente, e questa funzionalità lo rende istantaneo. Contatta il tuo team Vectra AI per partecipare all'anteprima privata e visitala pagina delle domande frequenti sull'integrazione EDR di Crowdstrikeper istruzioni su come supportare questa integrazione.
Scopri di più su come Vectra AI con CrowdStrike in questo podcast:
Vectra 360 Miglioramento della risposta per Cloud
Il blocco dell'accountVectra AI ora include la reimpostazione della password per AzureAD/Entra ID, fornendo ai clienti un modo più sicuro e affidabile per bloccare in modo proattivo gli attacchi basati sull'identità, in particolare il furto di token. Revocando le sessioni e forzando la reimpostazione della password, Vectra AI rimuove Vectra AI l'accesso degli aggressori, consentendo agli utenti legittimi di effettuare nuovamente l'accesso con il minimo sforzo. Ciò amplia la capacità di risposta a 360 gradi Vectra AI, che consente una risposta proattiva su traffico, dispositivi e identità. Per ulteriori informazioni sulla funzione, consultare l'articolo di supporto https://support.vectra.ai/vectra/article/KB-VS-1123. Per ulteriori informazioni sulla funzione, guardare:
Data:
Dicembre 2025
Rilascio:
9.7
QUX: Interfaccia apparecchiature
Copertura
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- Vectra AI riprogettando diverse firme Cobalt Strike come rilevamenti Python nativi. Trasferendo questi rilevamenti nel motore basato su Python di Vectra, tutti i clienti possono ora beneficiare della copertura Cobalt Strike senza dover fare affidamento sulla logica basata sulle firme.
- Vectra AI perfezionato il rilevamento dell'utilizzo di Kali Repo per migliorare la precisione e ridurre i falsi positivi, rendendo più rigorosa l'identificazione degli user agent correlati a Kali. Questo miglioramento concentra i criteri di corrispondenza sulla vera attività di Kali Linux, garantendo avvisi più accurati e informazioni più affidabili durante l'analisi dei potenziali strumenti utilizzati dagli aggressori.
- Vectra AI introdotto nuovi rilevamenti a livello informativo per gli strumenti di gestione e monitoraggio remoto (RMM) osservati negli ambienti dei clienti. Poiché le utility RMM vengono sempre più utilizzate negli attacchi informatici, questi avvisi forniscono visibilità sul loro utilizzo senza generare rumore o influire sul punteggio. Le notifiche vengono visualizzate nelle singole pagine Host, una per ogni sessione host, rimanendo nascoste nella pagina principale Rilevamenti a meno che non vengano modificati i filtri. Questo aggiornamento offre ai clienti una visione più chiara delle attività amministrative potenzialmente sensibili, mantenendo al contempo un'esperienza di avviso a basso impatto.
Chiarezza
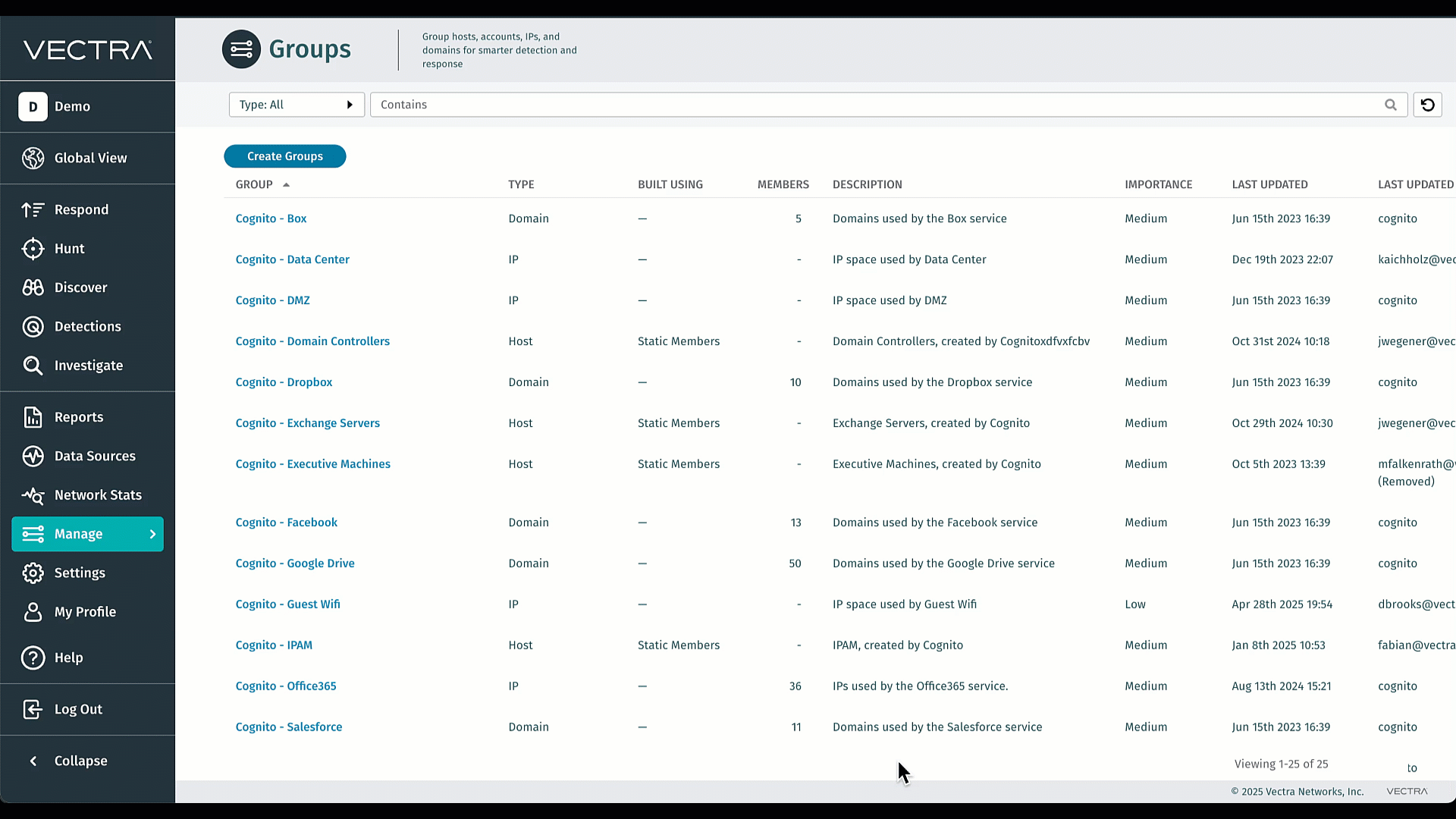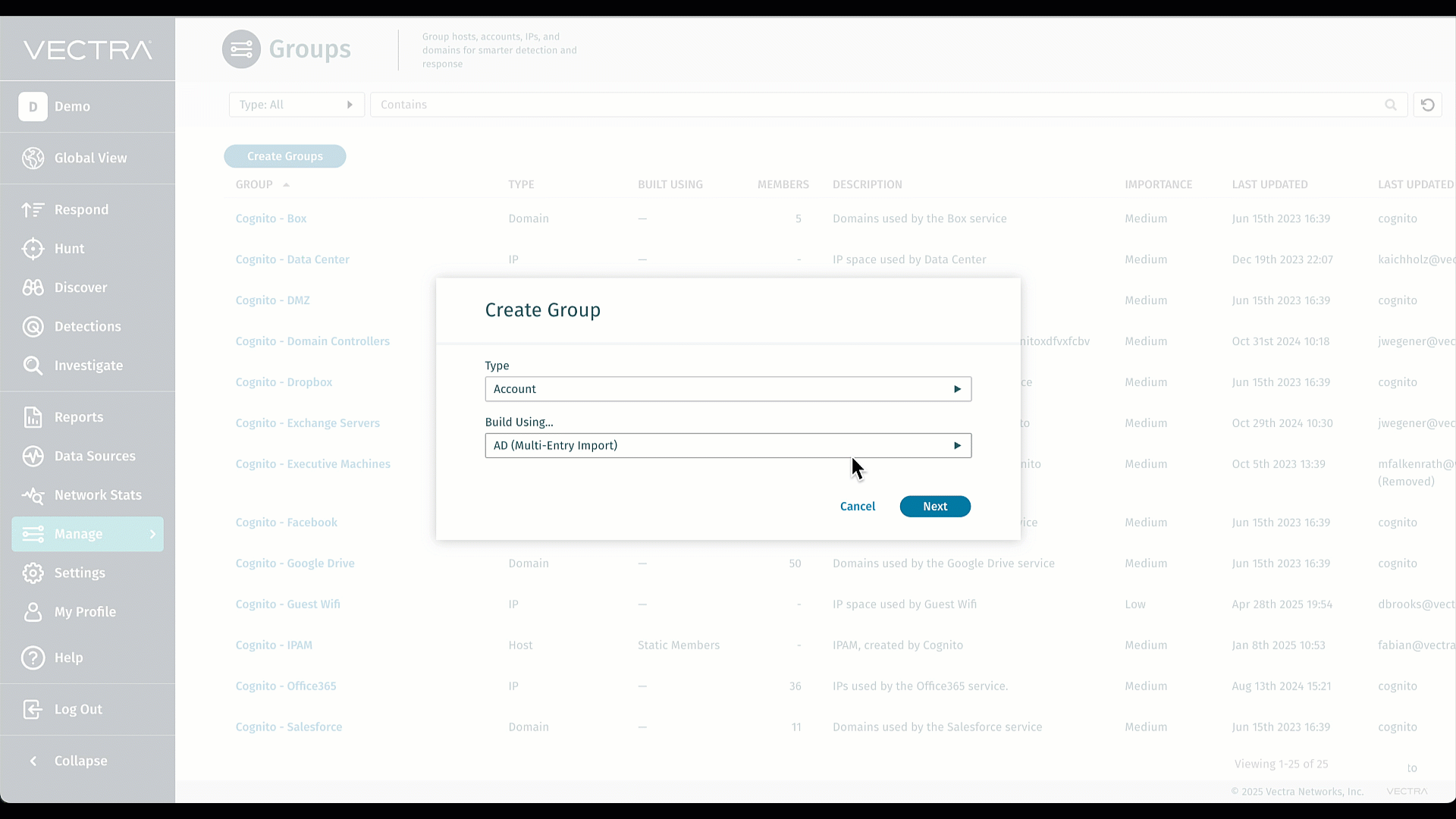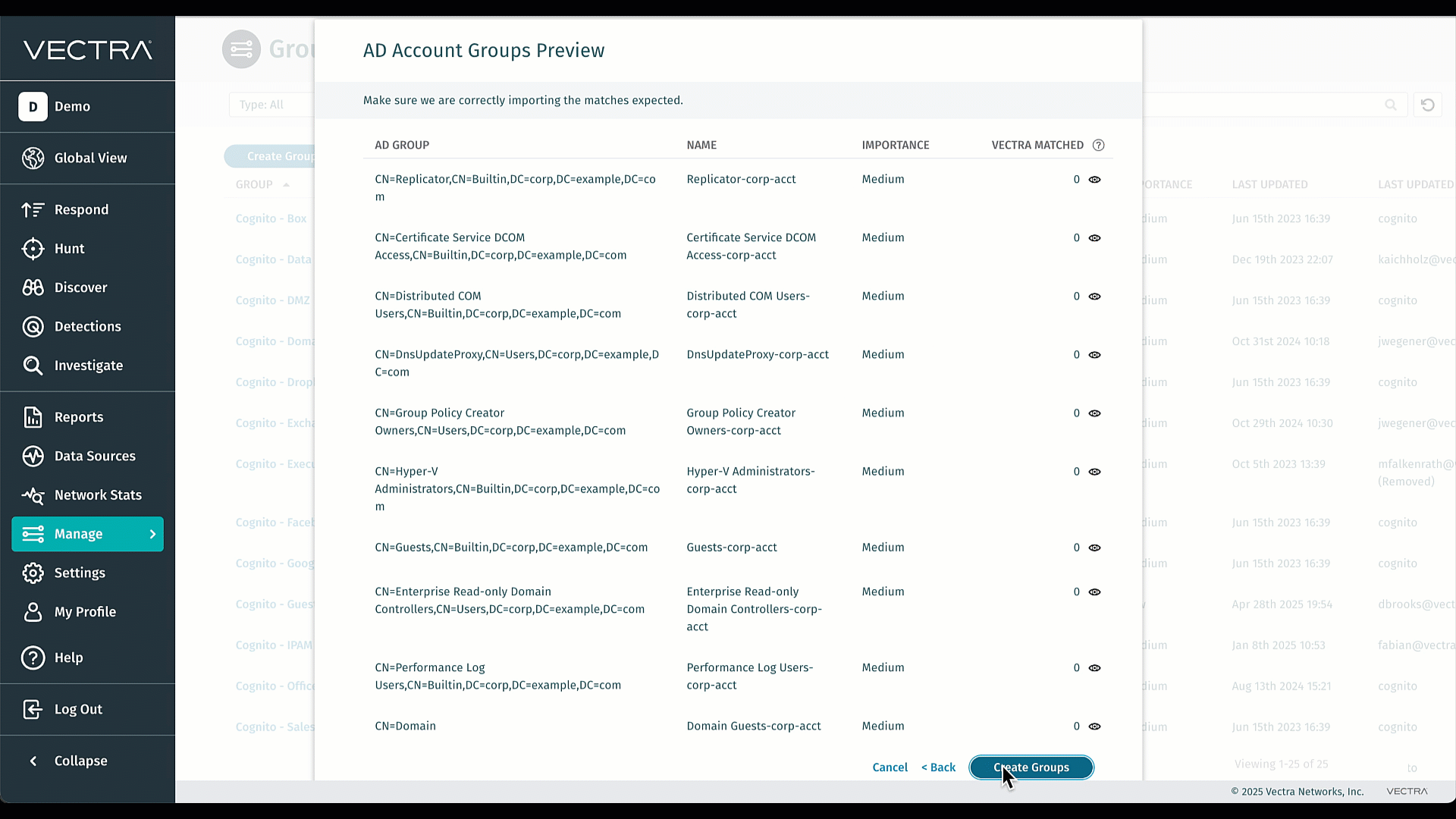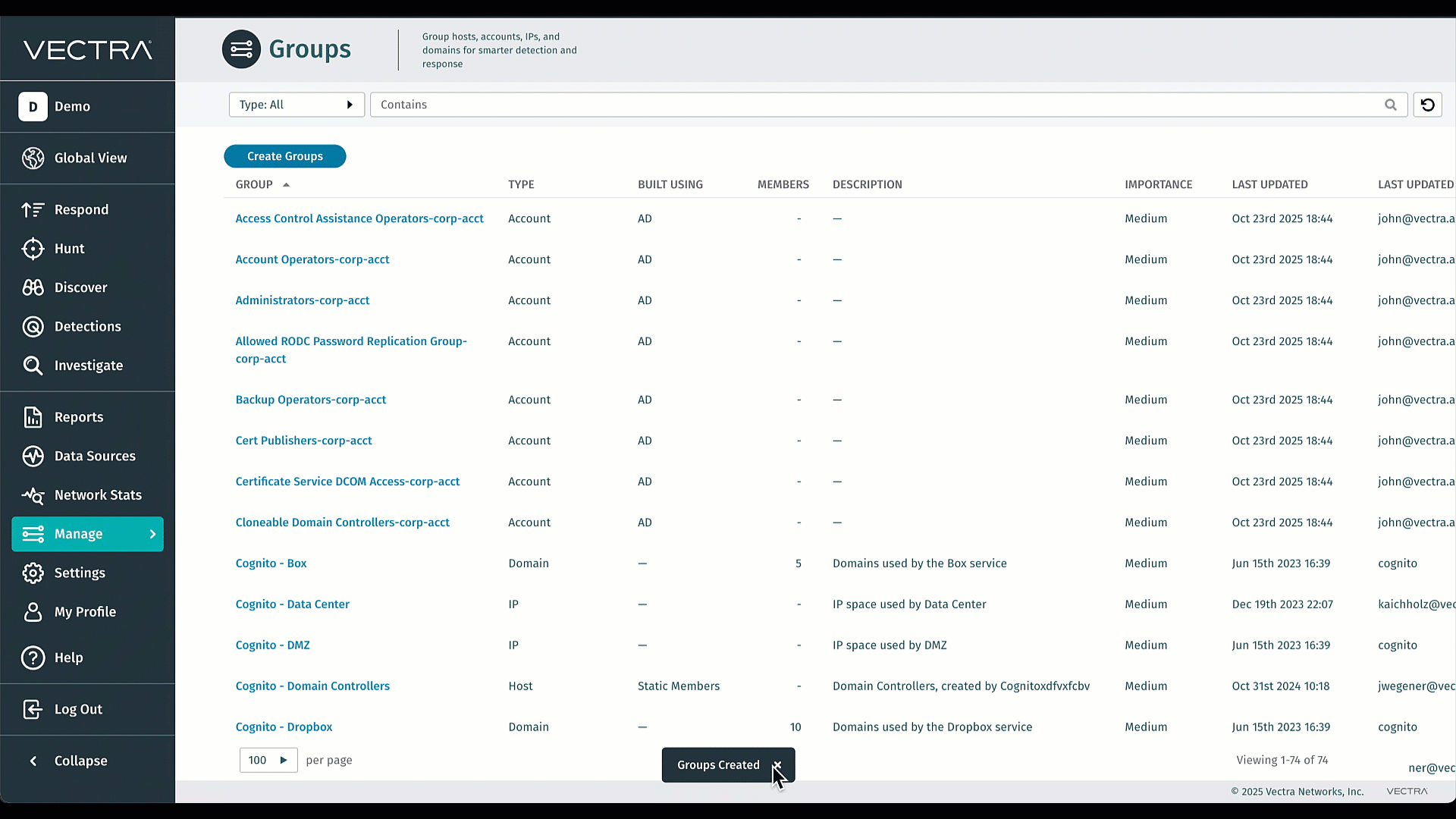
Gruppi basati sull'appartenenza ad Active Directory su Quadrant UX
Importa senza problemi i tuoi gruppi AD esistenti in Vectra e mantienili perfettamente sincronizzati: non dovrai più ricrearli manualmente né occuparti di noiose operazioni di manutenzione. L'importazione in blocco elimina il lavoro amministrativo ripetitivo, consentendo ai tuoi team di concentrarsi sulla ricerca delle minacce anziché sulla gestione dei gruppi. Ottimizzando le regole di triage e riducendo il rumore, potrai agire più rapidamente sugli avvisi che contano davvero. Si tratta di efficienza e chiarezza dei segnali, integrate direttamente nel sistema. Per ulteriori informazioni, visita la pagina Gruppi Active Directory (AD).
Agente di prioritizzazione del punteggio AI
L'agente di prioritizzazione AI ora rileva quando gli aggressori implementano nuovi sistemi, dai laptop non autorizzati ai Raspberry Pi, e ne tiene conto nella valutazione delle minacce.
Inoltre, apprende dalle tendenze storiche per segnalare i tipi di rilevamenti rari chiave nel tuo ambiente, fornendo una prioritizzazione più rapida e accurata con meno rumore.
Il cliente potrebbe vedere un numero limitato di host con punteggi aggiornati. Per ulteriori informazioni, guarda questo podcast: https://youtu.be/DvsvR57xCS8
Architettura/Amministrazione
Accesso solo HTTPS per iDRAC e pagina di stato Embryo
Nell'ambito del nostro impegno costante per la sicurezza della piattaforma, la versione 9.7 disabilita l'accesso alla porta 80 (HTTP) sia per l'interfaccia di gestione fuori banda iDRAC che per la pagina di stato Embryo (utilizzata durante la decrittografia e il provisioning pre-VHE).
Con questo aggiornamento, questi componenti sono ora accessibili esclusivamente tramite HTTPS (porta 443), eliminando il rischio di traffico HTTP non crittografato. I clienti non vedranno più la porta 80 aperta sui dispositivi Vectra, garantendo che tutte le comunicazioni siano crittografate per impostazione predefinita.
Questa modifica non richiede alcuna azione da parte degli utenti e mantiene tutti i sistemi allineati alle migliori pratiche di sicurezza moderne.
API REST v2.5 (Quadrant UX)
Vectra AI continua ad aggiornare l'API QUX con nuove funzionalità ogni mese. Per rimanere aggiornato sulle ultime funzionalità, visita il Changelog dell'API REST v2.5.
Data:
Novembre 2025
Rilascio:
2025.11
RUX: Fornitura SaaS
Copertura
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- Vectra AI riprogettando diverse firme Cobalt Strike come rilevamenti Python nativi. Trasferendo questi rilevamenti nel motore basato su Python di Vectra, tutti i clienti possono ora beneficiare della copertura Cobalt Strike senza dover fare affidamento sulla logica basata sulle firme.
- Vectra AI perfezionato il rilevamento dell'utilizzo di Kali Repo per migliorare la precisione e ridurre i falsi positivi, rendendo più rigorosa l'identificazione degli user agent correlati a Kali. Questo miglioramento concentra i criteri di corrispondenza sulla vera attività di Kali Linux, garantendo avvisi più accurati e informazioni più affidabili durante l'analisi dei potenziali strumenti utilizzati dagli aggressori.
- Vectra AI introdotto nuovi rilevamenti a livello informativo per gli strumenti di gestione e monitoraggio remoto (RMM) osservati negli ambienti dei clienti. Poiché le utility RMM vengono sempre più utilizzate negli attacchi informatici, questi avvisi forniscono visibilità sul loro utilizzo senza generare rumore o influire sul punteggio. Le notifiche vengono visualizzate nelle singole pagine Host, una per ogni sessione host, rimanendo nascoste nella pagina principale Rilevamenti a meno che non vengano modificati i filtri. Questo aggiornamento offre ai clienti una visione più chiara delle attività amministrative potenzialmente sensibili, mantenendo al contempo un'esperienza di avviso a basso impatto.
Chiarezza
Blocco del traffico: difesa automatizzata della rete tramite integrazione firewall (anteprima pubblica)
Vectra AI consente ai clienti di intervenire immediatamente sulle minacce rilevate con Traffic Lockdown, una nuova funzionalità che blocca automaticamente gli host dannosi a livello di firewall. Integrandosi direttamente con i firewall supportati, Vectra AI pubblica Vectra AI gli IP delle minacce per un'applicazione immediata senza necessità di regole manuali o configurazioni complesse. I team di sicurezza ottengono un contenimento più rapido, flussi di lavoro più puliti e una protezione più forte dove è più importante: ai margini della rete. Visita Traffic Lockdown per le istruzioni di configurazione.
_compressed.gif)
Controllo
Blocco del traffico: difesa automatizzata della rete tramite integrazione firewall (anteprima pubblica)
Vectra AI consente ai clienti di intervenire immediatamente sulle minacce rilevate con Traffic Lockdown, una nuova funzionalità che blocca automaticamente gli host dannosi a livello di firewall. Integrandosi direttamente con i firewall supportati, Vectra AI pubblica dinamicamente gli IP dei feed delle minacce per un'applicazione immediata senza necessità di regole manuali o configurazioni complesse. I team di sicurezza ottengono un contenimento più rapido, flussi di lavoro più puliti e una protezione più forte dove è più importante: ai margini della rete. VisitaTraffic Lockdownper le istruzioni di configurazione.
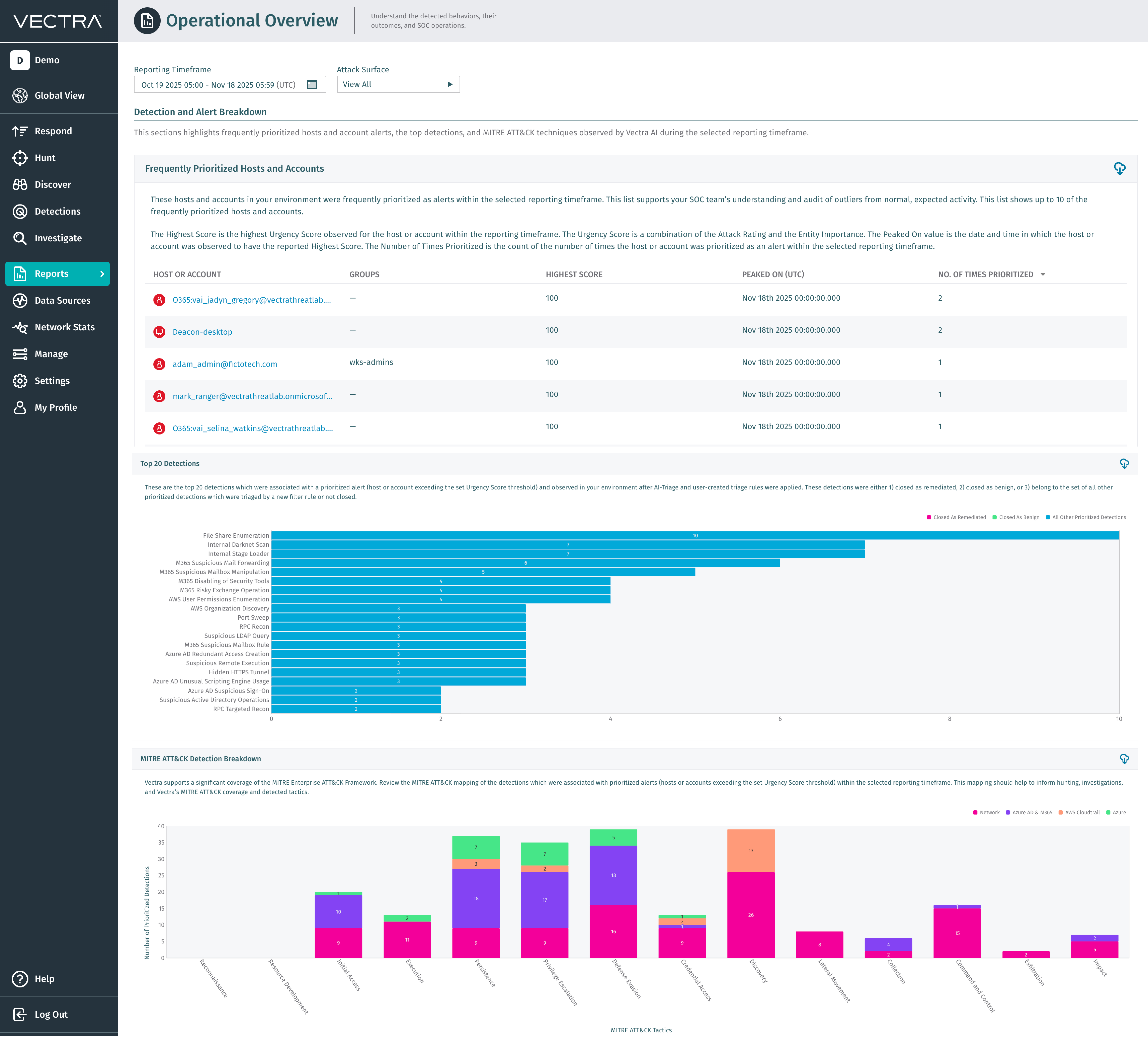
Relazione sulla panoramica operativa
Presentiamo il rapporto panoramica operativa, la nuova vista di comando del SOC per le prestazioni e l'impatto. Questo rapporto riunisce metriche chiave come il tempo medio di assegnazione, il tempo medio di indagine e il tempo medio di risoluzione, insieme alle principali rilevazioni, MITRE ATT&CK e alle entità prioritarie in un unico dashboard chiaro e visivo. Quantifica il modo in cui Vectra AI consente indagini più rapide, una selezione più accurata e guadagni di efficienza misurabili. Grazie a potenti approfondimenti per le revisioni aziendali, i report esecutivi e le operazioni quotidiane, trasforma i dati sulle prestazioni in una prova del valore.
Architettura/Amministrazione
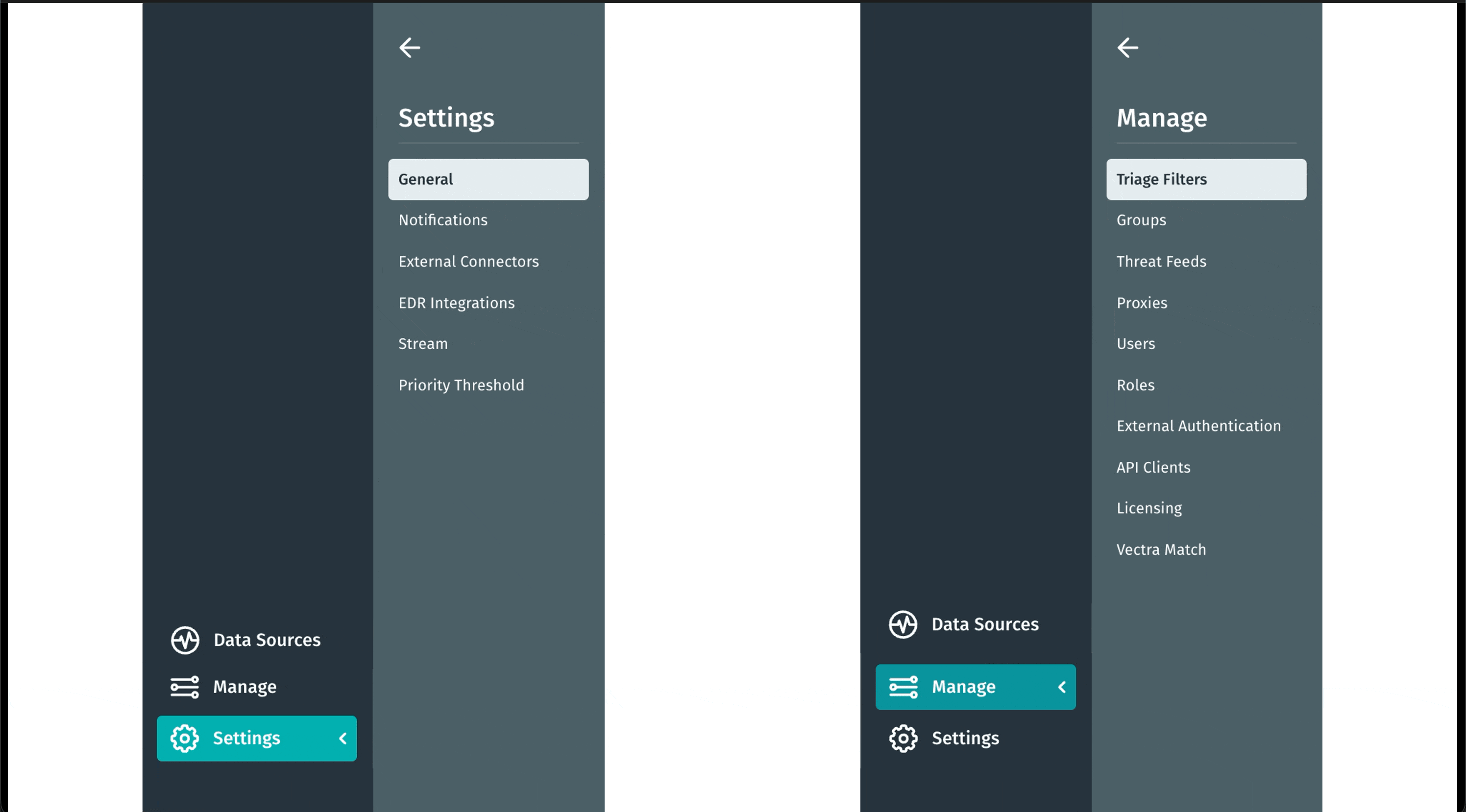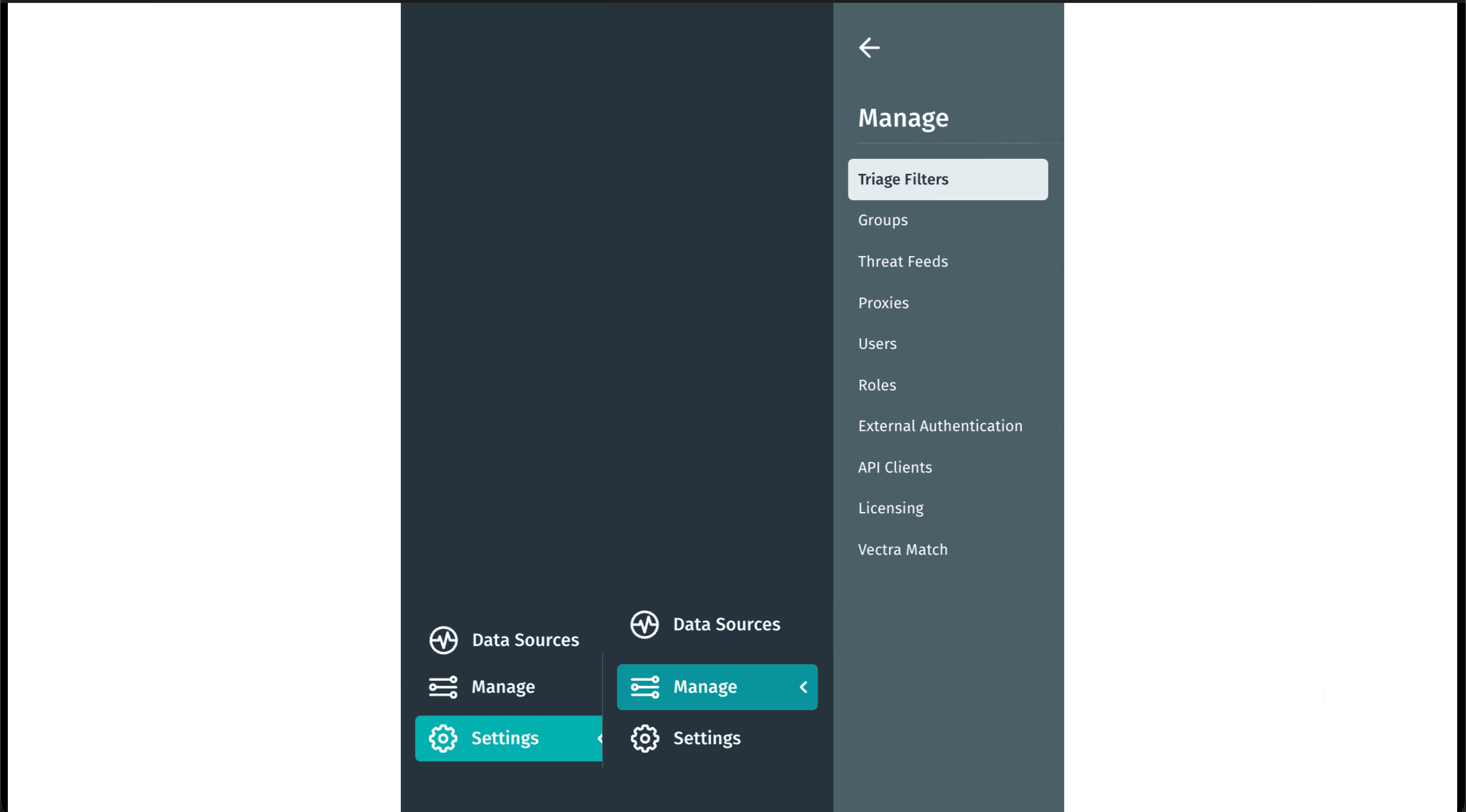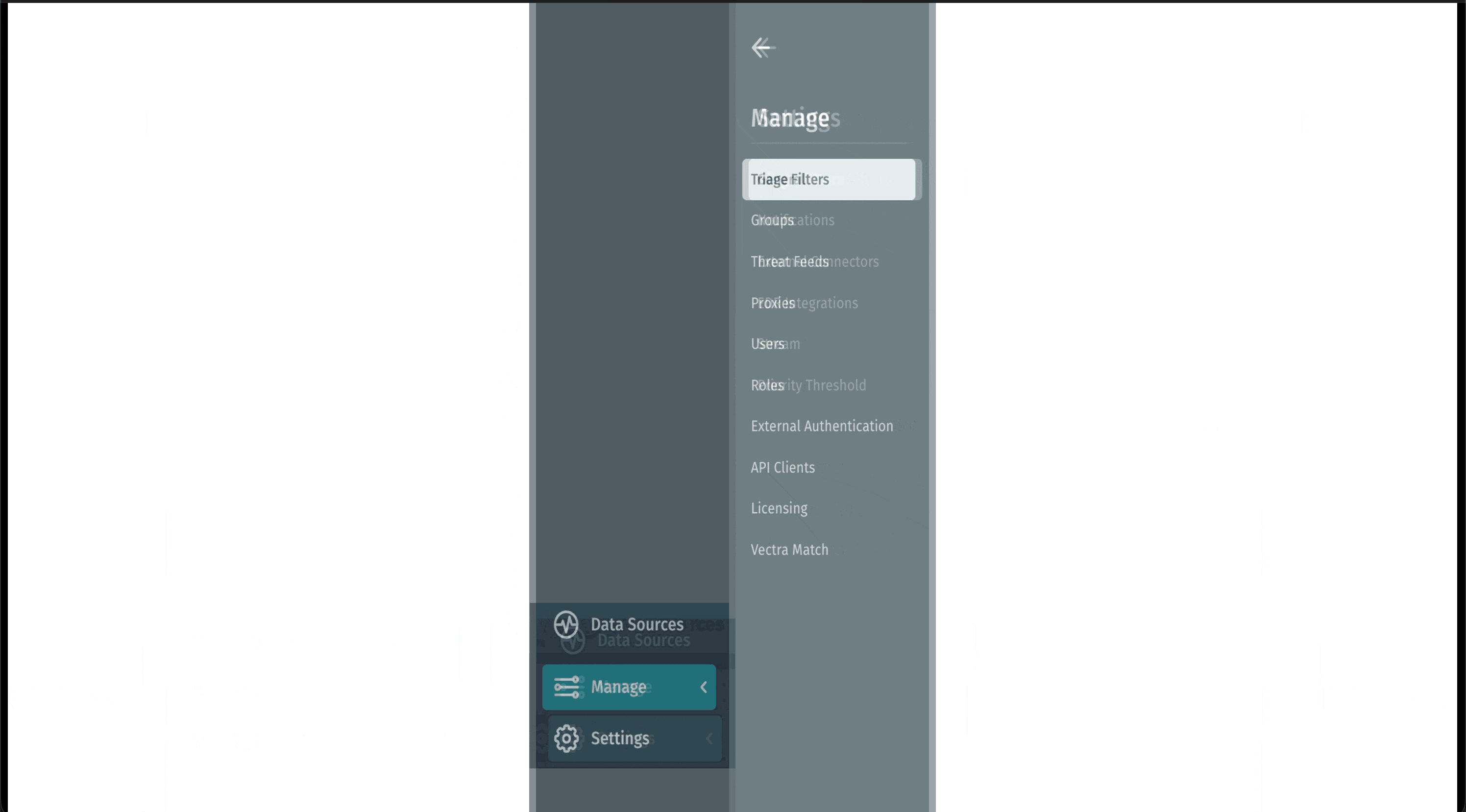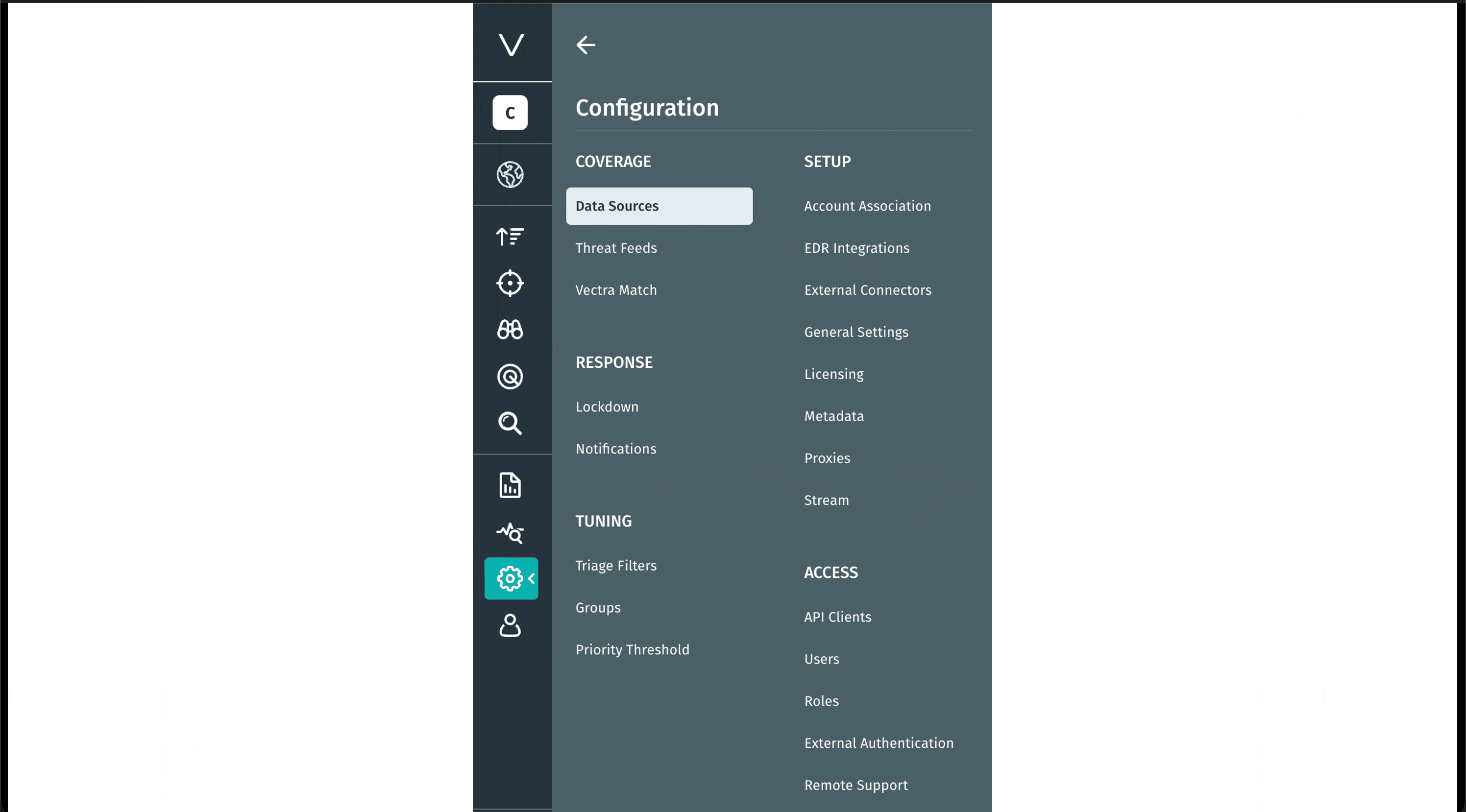
Modifica della navigazione: Configurazione
Abbiamo semplificato la gestione dell'ambiente nella Vectra AI . La nuovascheda Configurazioneunifica le opzioni Gestisci e Impostazioni per riunire tutte le impostazioni di configurazione e controllo in un'unica vista chiara e intuitiva, in modo da poter trovare più rapidamente ciò che serve e agire con sicurezza. Questo aggiornamento elimina gli attriti e semplifica la navigazione. Meno ricerche. Più risultati.
Supporto Multi-SAML
La piattaforma Respond UX attualmente supporta il Single Sign-On (SSO) attraverso l'integrazione con l'Identity Provider (IDP) del cliente utilizzando un profilo SAML configurato. Finora è possibile definire un solo profilo SAML, il che limita l'integrazione a un solo IDP alla volta.
Per risolvere questo problema, stiamo introducendo il supporto per più profili SAML. Questo miglioramento consentirà ai clienti e agli MSSP di configurare e gestire contemporaneamente le integrazioni con più IDP, garantendo una maggiore flessibilità e allineamento con ambienti di identità complessi.
Assistenza Accesso agli inquilini RUX
Abbiamo introdotto la possibilità per i dipendenti autorizzati Vectra AIdi accedere in modo sicuro alle interfacce utente dei tenant RUX quando necessario. I clienti possono ora configurare una data di scadenza per questo accesso, assicurandosi che rimanga limitato nel tempo e completamente sotto il loro controllo.

API REST (Respond UX)
Vectra AI continua ad aggiornare l'API RUX con nuove funzionalità ogni mese. Per rimanere aggiornato sulle ultime funzionalità, visita il nostro sito di documentazione API.
Data:
Novembre 2025
Rilascio:
9.6
QUX: Interfaccia apparecchiature
Copertura
Integrazione Netskope SASE in anteprima pubblica
Man mano che gli utenti e le applicazioni si spostano oltre il perimetro aziendale, i difensori perdono visibilità sul traffico critico che fluisce direttamente verso il cloud. Ciò crea punti ciechi in cui possono nascondersi comandi e controlli avanzati (C2) e l'esfiltrazione dei dati, lasciando le organizzazioni esposte.
La nuova integrazione Vectra AIcon Netskope CloudTAP colma questa lacuna. Ricevendo il traffico GENEVE da Netskope Stitcher, Vectra offre agli utenti remoti e cloud lo stesso livello di rilevamento approfondito delle minacce e visibilità dei metadati garantito agli utenti on-premise, eliminando i punti ciechi nei moderni ambienti SASE.
Se sei interessato ad abilitare l'integrazione Netskope di Vectra, contatta il team responsabile del tuo account Vectra. Per i dettagli sull'implementazione, consulta Netskope SASE Integration and Optimization (Integrazione e ottimizzazione SASE di Netskope).
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- Vectra AI rileva le query LDAP rivolte agli account Active Directory che non dispongono della pre-autenticazione Kerberos, una fase comune negli attacchi AS-REP roasting. Questo miglioramento offre una visibilità più tempestiva sulla ricognizione delle credenziali, aiutando i team di sicurezza a fermare gli aggressori prima che inizi l'abuso delle credenziali.
- Vectra AI perfezionato la sua logica di rilevamento delle attività di brute force RDP e password spray per migliorare la precisione e ridurre i falsi positivi in ambienti con host condivisi o bastion. Il miglioramento chiarisce le soglie di rilevamento e le descrizioni, garantendo ai clienti avvisi più accurati e informazioni più utili durante le indagini su potenziali comportamenti di brute force.
- Vectra AI migliorato l'analisi LDAP per identificare la ricognizione degli utenti AD con nomi principali di servizio (SPN), un precursore del Kerberoasting. Questo aggiornamento consente un rilevamento più rapido degli attacchi mirati alle credenziali, offrendo ai clienti una visibilità più approfondita delle minacce nascoste di Active Directory.
Chiarezza
JA4T/JA4TS Impronte digitali: Recall Stream
Vectra AI include le impronte digitali JA4T (TCP Client) e JA4TS (TCP Server) nei metadati, introducendo il fingerprinting di nuova generazione nell'analisi del traffico crittografato. Questo potente framework riduce le collisioni, collega le sessioni correlate e rende più facile individuare l'infrastruttura degli aggressori nascosta dietro protocolli comuni. Gli analisti ottengono informazioni più chiare e rapide con meno rumore e un contesto migliore tra i rilevamenti. Le impronte digitali JA4T/JA4TS sono ora supportate in Stream e Recall, mentre JA4T/JA4TS sarà aggiunto ad Advanced Investigate (RUX) entro la fine dell'anno. Maggiori informazioni sui nuovi attributi sono disponibili qui.
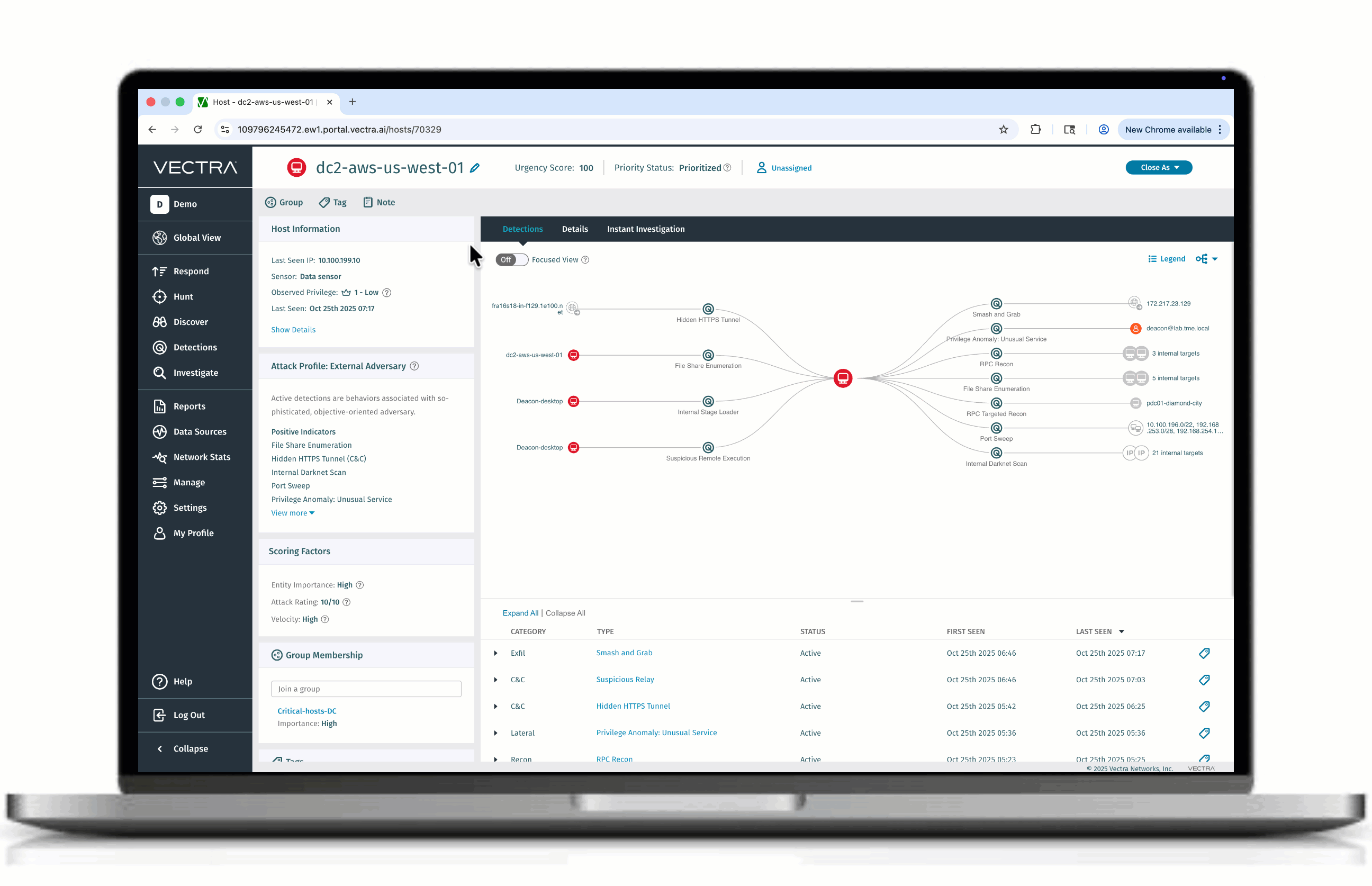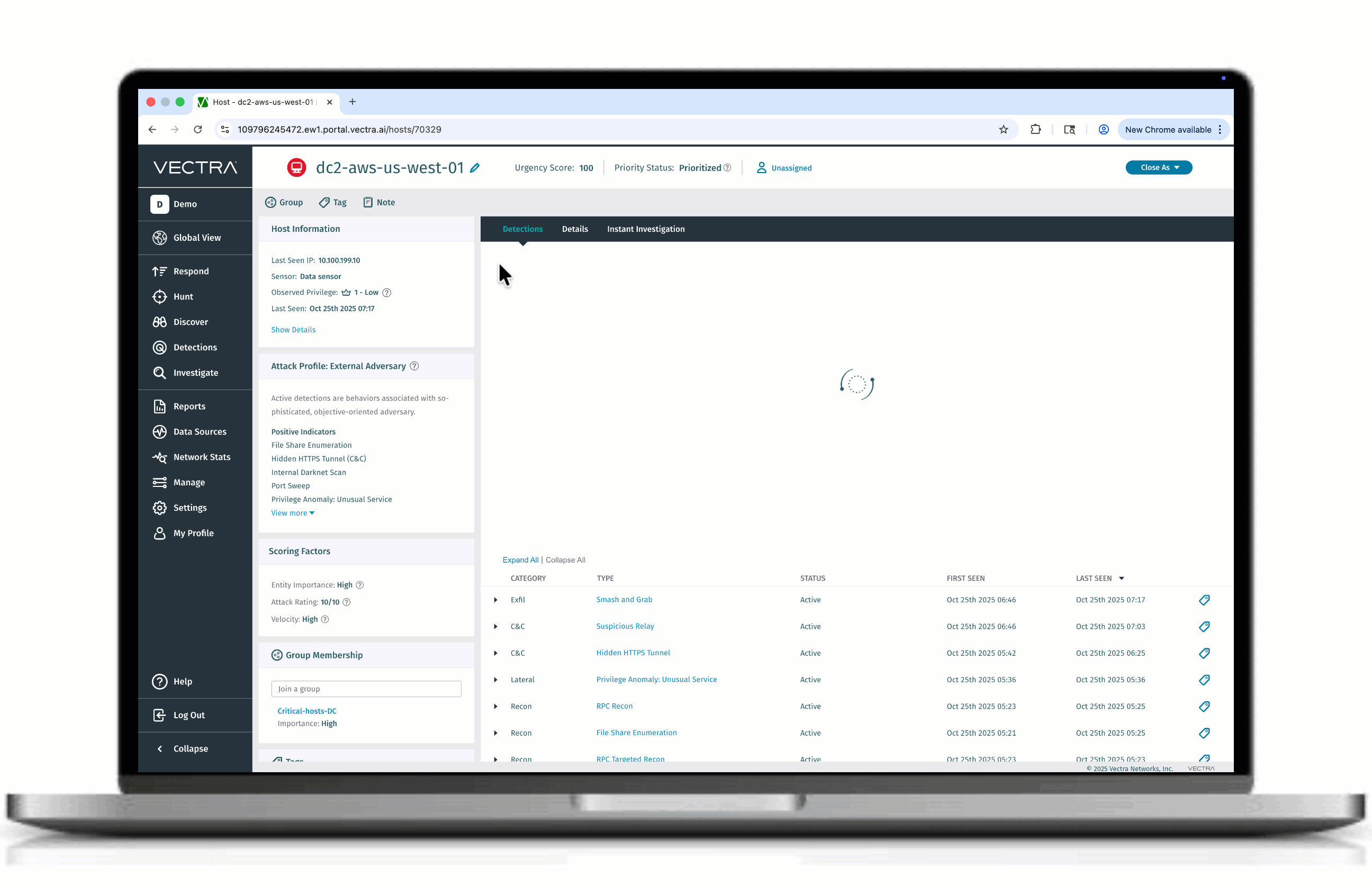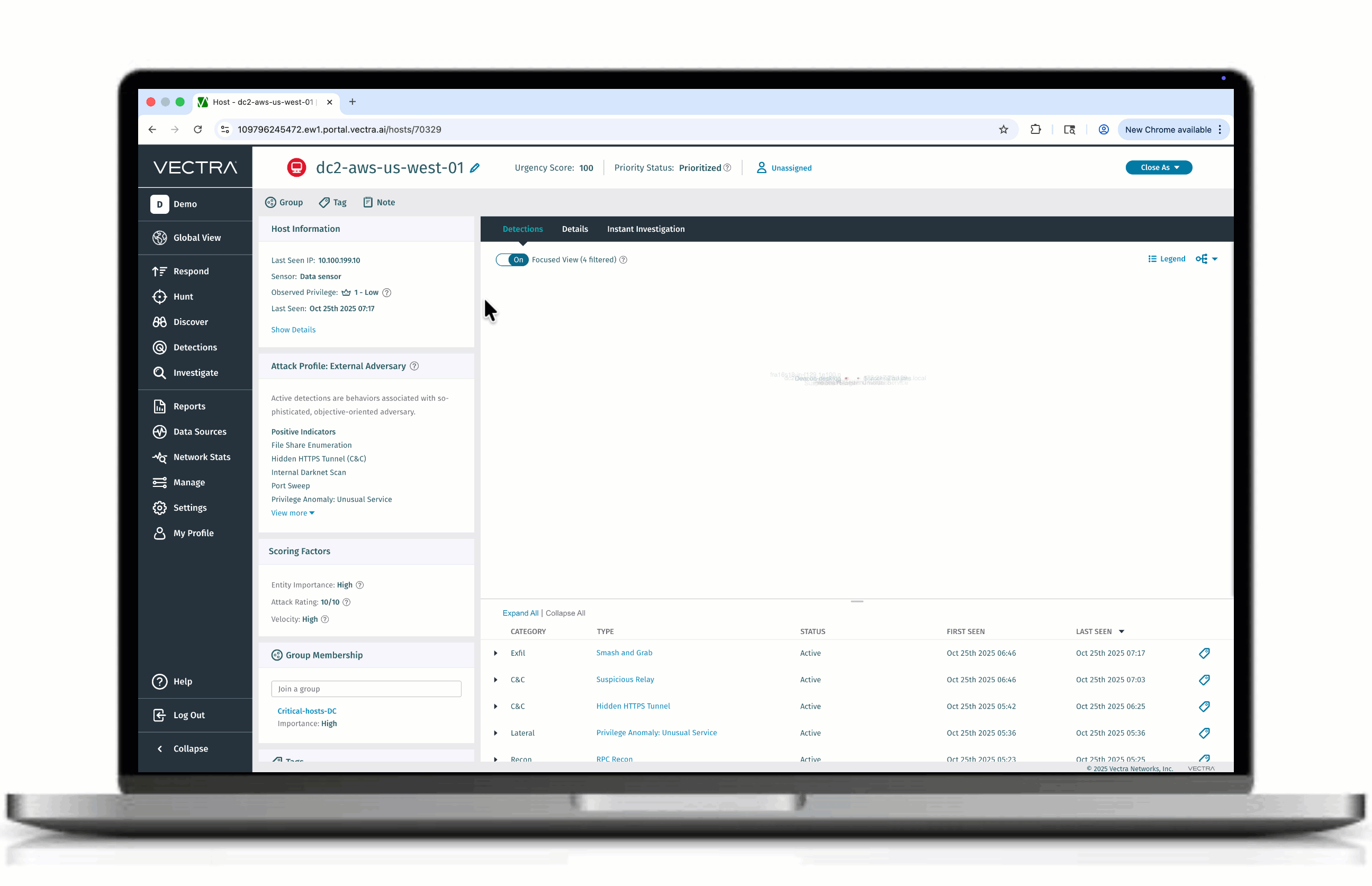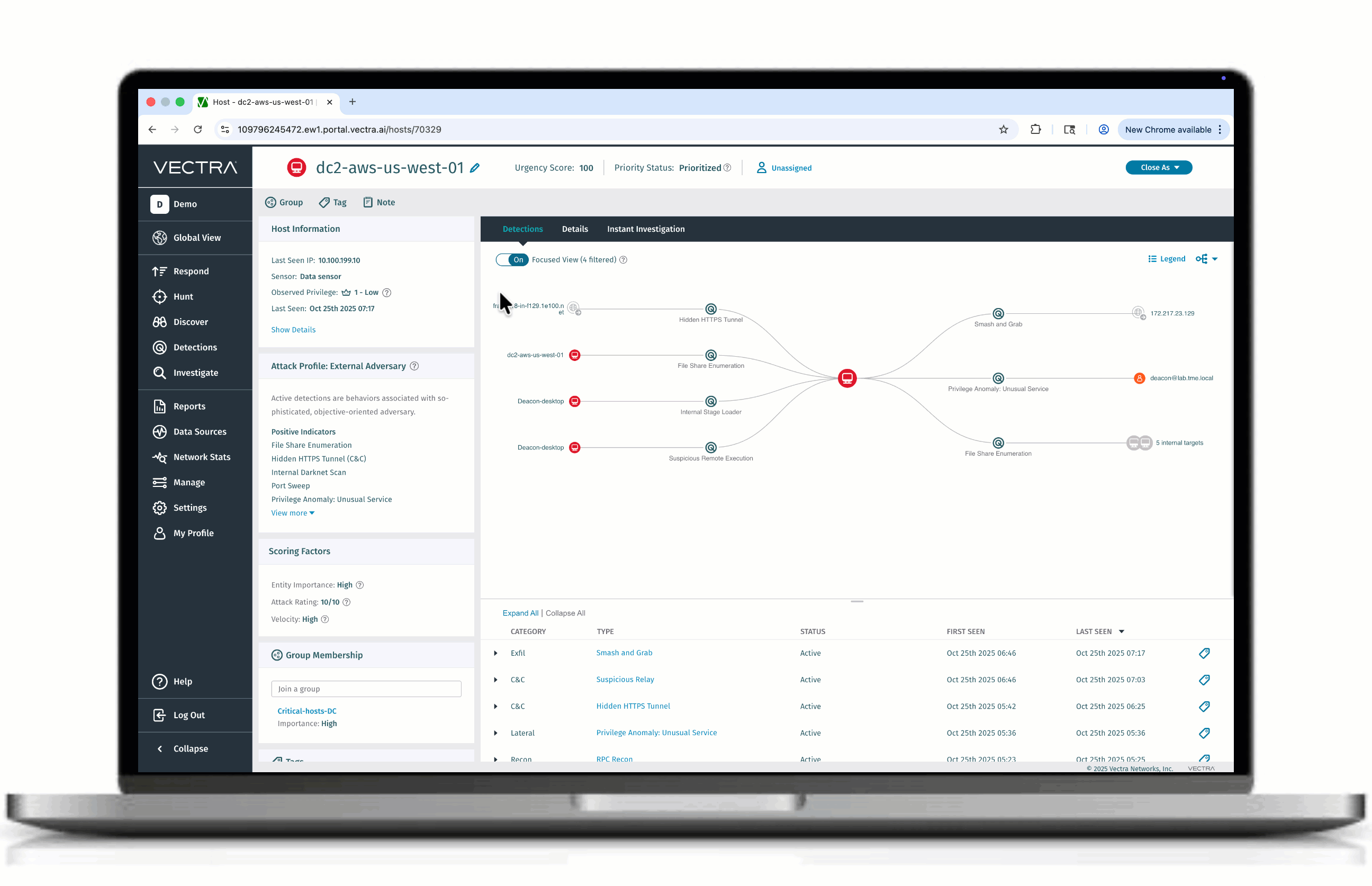
Grafico degli attacchi: vista focalizzata
Presentiamo Focused View, un nuovo modo per eliminare il rumore dai complessi grafici degli attacchi. Anziché sovraccaricare gli analisti con ogni nodo e ogni bordo, Focused View filtra i rilevamenti a bassa priorità e mostra solo i collegamenti e i percorsi di progressione più critici. Il risultato: meno confusione, meno disordine e una prospettiva chiara su come si è svolto un attacco. Grazie alla chiarezza anziché al disordine, i team di sicurezza possono accelerare le indagini, passando comunque al grafico completo quando necessario.
Architettura/ Amministrazione
Presentazione del Vectra Virtual Brain per Nutanix
Vectra offre ora un dispositivo Brain completamente virtualizzato per gli ambienti Nutanix. Disponibile con una velocità di trasmissione di 10 Gbps, questo Brain virtuale offre le stesse funzionalità avanzate dei dispositivi fisici, ottimizzate per la scalabilità, la rapida implementazione e l'efficienza operativa. Per le specifiche dettagliate e le configurazioni supportate, consultare la guida alle specifiche dei dispositivi e dei sensori. Per le istruzioni di implementazione, consultare la guida all'implementazione di Nutanix.
Sicurezza potenziata: accesso solo HTTPS all'interfaccia utente Vectra
Per rafforzare la sicurezza della piattaforma, l'interfaccia utente di Vectra ora blocca l'accesso esterno sulla porta 80 (HTTP) invece di reindirizzare automaticamente alla porta 443 (HTTPS) come avveniva in precedenza. Con questo aggiornamento, l'interfaccia utente di Vectra sarà ora accessibile esclusivamente tramite HTTPS, rafforzando ulteriormente la sicurezza della piattaforma e garantendo che tutte le connessioni siano crittografate per impostazione predefinita. Questo aggiornamento si applica solo a Vectra Brain e non richiede alcuna azione da parte degli utenti, mantenendo il vostro ambiente in linea con le migliori pratiche di sicurezza moderne.
Data:
Ottobre 2025
Rilascio:
9.5
QUX: Interfaccia apparecchiature
Copertura
Command and Control Sliver
Vectra AI introdotto una nuova copertura di rilevamento per l'attività Sliver Command & Control C2), un framework avanzato utilizzato dai red team e dagli autori delle minacce per eludere le difese tradizionali. L'uso da parte di Sliver di crittografia, codificatori a più livelli e modelli di temporizzazione e dati variabili gli consente di mascherare i beaconing dannosi all'interno del normale traffico crittografato. Il modello di deep learning di Vectra identifica questi modelli sottili senza fare affidamento sull'ispezione del payload, sfruttando il più grande set di dati del settore sul comportamento della rete. Questo aggiornamento migliora i nostri attuali algoritmi di beaconing C2, offrendo una maggiore visibilità sui canali C2 evasivi e aiutando i team di sicurezza a rilevare le attività sofisticate degli avversari in una fase più precoce della catena di attacco.
Nuovo rilevamento: modifica della registrazione delle VM sospette in Azure
Vectra AI introdotto una nuova funzione di rilevamento che individua comportamenti sospetti legati alla modifica delle estensioni di registrazione per macchine virtuali Windows e Linux, set di macchine virtuali scalabili e macchine ibride. Ciò fornisce una visibilità più approfondita sulle attività sospette che potrebbero indicare tentativi di manomissione del monitoraggio della sicurezza (registri degradati rispetto a quelli completamente disabilitati).
Miglioramento del rilevamento: Azure Cryptomining
Sono stati introdotti miglioramenti al rilevamento Azure Cryptomining per filtrare i comportamenti legati alla modifica delle istanze di calcolo esistenti. Questo miglioramento aumenta l'affidabilità degli avvisi relativi alla creazione di nuove istanze di calcolo. I clienti dovrebbero aspettarsi un numero inferiore di avvisi legati a questo comportamento nel proprio ambiente.
Miglioramenti al rilevamento di M365
Sono stati introdotti miglioramenti nei seguenti rilevamenti per ampliare la copertura:
- Creazione di regole per caselle di posta sospette in M365 e inoltro di posta sospetta in M365: questi rilevamenti sono stati migliorati per includere la copertura dei comportamenti relativi a UpdateInboxRule. Come risultato di questo miglioramento, i clienti potrebbero osservare un leggero aumento dei volumi associati a questi avvisi.
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- NDR-242: Vectra AI ampliato Command & Control suoi attuali Command & Control per rilevare tecniche avanzate di segnalazione C2 che utilizzano dati e jitter temporale per eludere il monitoraggio tradizionale della rete. Il risultato è una maggiore visibilità sul comportamento furtivo del C2 e un rilevamento più tempestivo delle minacce sofisticate che tentano di nascondersi all'interno della normale attività di rete.
- NDR-302: Vectra AI migliorato la copertura di rilevamento per le comunicazioni TCP in testo semplice, identificando attività di comando sospette nascoste nel traffico non crittografato basato su testo. Questo aggiornamento rileva modelli comportamentali sottili, come flussi di pacchetti anomali e strutture di payload, per scoprire canali di comando nascosti che eludono le ispezioni tradizionali. Espande la visibilità oltre il traffico crittografato, rafforzando il rilevamento su tutti i tipi di comunicazione.
- NDR-314: Vectra AI ampliato la copertura per includere il canale HTTP inglese di Sliver, che maschera il traffico di comando e controllo come stringhe di parole inglesi casuali per apparire legittimo. Questo miglioramento ottimizza il rilevamento delle attività Sliver offuscate all'interno del normale traffico HTTP, rafforzando la visibilità sulle tecniche avanzate di evasione C2.
Chiarezza
Volume di allerta ridotto con triage AI potenziato
AI-Triage di Vectra offre ora funzionalità ampliate lungo tutta la catena di attacco e nelle reti moderne, riducendo significativamente i volumi di rilevamento. Indaga e risolve automaticamente gli avvisi benigni, riducendo l'affaticamento da avvisi e preservando al contempo la piena visibilità sulle minacce reali.
Questa funzionalità personalizzata e rigorosamente testata identifica i modelli a basso rischio che compaiono costantemente nel tuo ambiente e li risolve automaticamente, consentendo al tuo team di concentrarsi sui rischi significativi.
Aspettati meno rilevamenti benigni su rete C2, ricognizione, Azure AD, M365, Copilot per M365 e AWS.
La visibilità non viene mai persa: i rilevamenti risolti rimangono ricercabili, verificabili e completamente tracciabili. Non vengono intraprese azioni per conto dell'utente oltre alla risoluzione.
Prossimamente: contesto di processo EDR ampliato
A novembre, Vectra rilascerà Vectra AI con CrowdStrike EDR per tutti i clienti. Questa funzionalità semplifica le indagini individuando automaticamente il processo probabile correlato a un rilevamento NDR e presentandolo insieme al rilevamento nella piattaforma e quando l'evento viene raccolto tramite API.
Il risultato è un NDR più potente, meno lavoro manuale e risultati migliori per i team di sicurezza. Qual era il processo che guidava C2, un browser o uno script PowerShell? È prevedibile o si tratta di un caso eccezionale? Queste sono domande a cui gli analisti devono rispondere immediatamente, e questa funzionalità rende possibile farlo all'istante.
Per garantire la corretta erogazione di questa funzionalità, invitiamo tutti i clienti Crowdstrike a fornire le autorizzazioni NGSIEM Read / NGSIEM Write per supportare la futura raccolta di queste informazioni. Visitate la pagina Domande frequenti sull'integrazione EDR di Crowdstrike per istruzioni su come concedere queste autorizzazioni.
Controllo
Miglioramenti al grafico degli attacchi
L'Attack Graph Vectra AIè diventato ancora più intelligente grazie a due potenti aggiornamenti. C2 Blast Radius rivela istantaneamente tutti gli host che comunicano con lo stesso endpoint di comando e controllo, eliminando i riferimenti incrociati manuali e velocizzando la selezione. I rilevamenti mirati tracciano il punto iniziale di compromissione e i movimenti dell'autore dell'attacco, fornendo agli analisti una chiara ricostruzione di come è stato raggiunto ogni host o account. Insieme, questi miglioramenti offrono una visibilità più nitida, indagini più rapide e risposte più precise. Esplora le domande frequenti sull'Attack Graph per ulteriori funzionalità.
Architettura / Amministrazione
Verifica file SHA256 per il portale di assistenza
Tutti i file attuali e futuri presenti nella sezione Risorse aggiuntive > Download del nostro portale di assistenza ora includono un hash SHA256 per verificare che il file scaricato sia identico a quello fornito dal portale di assistenza. Attualmente questo vale per i download Match OVA e Vectra Match .
Riconoscimento crittografico TLS/SSL esteso
Vectra AI ampliato la mappatura della suite di cifratura TLS/SSL per includere l'ultimo TLS 1.3 e le moderne suite di cifratura, garantendo che le sessioni crittografate siano identificate con precisione e visualizzate con nomi chiari e leggibili. Questo aggiornamento migliora la visibilità e l'accuratezza nell'analisi del traffico crittografato su Recall Stream, con il supporto di Advanced Investigations previsto per una versione futura.
Data:
Ottobre 2025
Rilascio:
2025.10
RUX: Fornitura SaaS
Copertura
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- Vectra AI rileva le query LDAP rivolte agli account Active Directory che non dispongono della pre-autenticazione Kerberos, una fase comune negli attacchi AS-REP roasting. Questo miglioramento offre una visibilità più tempestiva sulla ricognizione delle credenziali, aiutando i team di sicurezza a fermare gli aggressori prima che inizi l'abuso delle credenziali.
- Vectra AI aggiornato la descrizione del suo rilevamento di attacchi brute-force e password-spray RDP per allinearla meglio al suo comportamento di rilevamento. Sebbene la logica di base rimanga invariata, la descrizione rivista chiarisce come l'attività di password-spray viene rappresentata nell'interfaccia utente, aiutando gli analisti a interpretare gli avvisi con maggiore precisione.
- Vectra AI migliorato l'analisi LDAP per identificare la ricognizione degli utenti AD con servicePrincipalNames (SPN), un precursore del Kerberoasting. Questo aggiornamento consente un rilevamento più rapido degli attacchi mirati alle credenziali, offrendo ai clienti una visibilità più approfondita delle minacce nascoste di Active Directory.
Chiarezza
Presentazione della ricerca assistita dall'intelligenza artificiale
Stiamo rendendo la ricerca e l'analisi delle minacce più veloce e intelligente. Con la ricerca assistita dall'intelligenza artificiale, è possibile porre domande in linguaggio semplice, in qualsiasi lingua principale, e ottenere immediatamente risposte ricche di contesto, approfondimenti visivi e consigli sui passi successivi da intraprendere. Nessuna sintassi di query, nessuna congettura: solo informazioni utili a portata di mano. I primi utenti hanno ridotto i tempi di indagine fino a tre ore per caso, scoprendo esposizioni che avrebbero potuto trascurare. Disponibile ora per i clienti RUX con almeno 14 giorni di metadati.
.gif)
Agente di prioritizzazione AI
L'agente di prioritizzazione AI ora rileva quando gli aggressori implementano nuovi sistemi, dai laptop non autorizzati ai Raspberry Pi, e ne tiene conto nella valutazione delle minacce.
Inoltre, apprende dalle tendenze storiche per segnalare i tipi di rilevamenti rari chiave nel tuo ambiente, fornendo una prioritizzazione più rapida e accurata con meno rumore.
Il cliente potrebbe vedere un numero limitato di host con punteggi aggiornati. Per ulteriori informazioni, guarda questo prodcast. https://youtu.be/DvsvR57xCS8
Architettura e amministrazione
Gruppi basati sull'appartenenza ad Active Directory
Importa senza problemi i tuoi gruppi AD esistenti in Vectra e mantienili perfettamente sincronizzati: non dovrai più ricrearli manualmente né occuparti di noiose operazioni di manutenzione. L'importazione in blocco elimina il lavoro amministrativo ripetitivo, consentendo ai tuoi team di concentrarsi sulla ricerca delle minacce anziché sulla gestione dei gruppi. Ottimizzando le regole di triage e riducendo il rumore, potrai agire più rapidamente sugli avvisi che contano davvero. Si tratta di efficienza e chiarezza dei segnali, integrate direttamente nel sistema. Per ulteriori informazioni, visita la pagina Gruppi Active Directory (AD).

È disponibile la nuova documentazione API REST
Siamo lieti di presentare il nuovo portale di documentazione API REST di Vectra, la soluzione completa per creare, testare e integrare le API di Vectra più rapidamente che mai.
RAD sostituisce i PDF statici con una documentazione OpenAPI dinamica e sempre accurata, completa di un client integrato per provare le richieste direttamente dal browser.
Gli sviluppatori possono ora esplorare, convalidare e generare integrazioni senza soluzione di continuità, garantendo un'automazione più rapida, meno errori e una maggiore sicurezza nell'ambiente.
A partire dalla versione API v3.5, tutta la documentazione sarà fornita esclusivamente tramite il portale della documentazione REST API: https://apidocs.vectra.ai
Data:
Settembre 2025
Rilascio:
2025.09
RUX: Fornitura SaaS
Copertura
Command and Control Sliver
Vectra AI ampliato la copertura per includere il canale HTTP inglese di Sliver, che maschera il traffico di comando e controllo sotto forma di stringhe di parole inglesi casuali per apparire legittimo. Questo miglioramento ottimizza il rilevamento delle attività offuscate di Sliver all'interno del normale traffico HTTP, rafforzando la visibilità sulle tecniche avanzate di evasione C2.
Command and Control TCP
Vectra AI migliorato la copertura di rilevamento per le comunicazioni TCP in testo semplice, identificando attività di comando sospette nascoste nel traffico non crittografato e basato su testo. Questo aggiornamento rileva modelli comportamentali sottili, come flussi di pacchetti anomali e strutture di payload, per scoprire canali di comando nascosti che eludono le ispezioni tradizionali. Espande la visibilità oltre il traffico crittografato, rafforzando il rilevamento su tutti i tipi di comunicazione.
Nuovo rilevamento: modifica della registrazione delle VM sospette in Azure
Vectra AI introdotto una nuova funzione di rilevamento che individua comportamenti sospetti legati alla modifica delle estensioni di registrazione per macchine virtuali Windows e Linux, set di macchine virtuali scalabili e macchine ibride. Ciò fornisce una visibilità più approfondita sulle attività sospette che potrebbero indicare tentativi di manomissione del monitoraggio della sicurezza (registri degradati rispetto a quelli completamente disabilitati).
Miglioramento del rilevamento: Azure Cryptomining
Sono stati introdotti miglioramenti al rilevamento Azure Cryptomining per filtrare i comportamenti legati alla modifica delle istanze di calcolo esistenti. Questo miglioramento aumenta l'affidabilità degli avvisi relativi alla creazione di nuove istanze di calcolo. I clienti dovrebbero aspettarsi un numero inferiore di avvisi legati a questo comportamento nel proprio ambiente.
Espansione della registrazione delle risorse per l'account di archiviazione (CDR per Azure)
Vectra AI ora i log delle risorse Azure collegati agli account di archiviazione a supporto dei casi d'uso di rilevamento nuovi e futuri. Questi nuovi log consentiranno a Vectra di rilevare i comportamenti di impatto ed esfiltrazione osservati nelle fasi finali della cloud . Tutti i nuovi connettori CDR per Azure accumuleranno automaticamente i log come parte della configurazione del connettore. Per i clienti CDR per Azure esistenti, sarà necessario rieseguire gli script di distribuzione automatizzata associati a CDR per Azure. I team di account Vectra contatteranno i clienti esistenti per facilitare l'espansione della registrazione.
Miglioramenti al rilevamento di M365
Sono stati introdotti miglioramenti nei seguenti rilevamenti per ampliare la copertura:
- Creazione di regole per caselle di posta sospette in M365 e inoltro di posta sospetta in M365: questi rilevamenti sono stati migliorati per includere la copertura dei comportamenti relativi a UpdateInboxRule. Come risultato di questo miglioramento, i clienti potrebbero osservare un leggero aumento dei volumi legati a questi avvisi.
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte di questa versione:
- NDR-242: Vectra AI ampliato Command & Control suoi attuali Command & Control per rilevare tecniche avanzate di segnalazione C2 che utilizzano dati e jitter temporale per eludere il monitoraggio tradizionale della rete. Il risultato è una maggiore visibilità sul comportamento furtivo del C2 e un rilevamento più tempestivo delle minacce sofisticate che tentano di nascondersi all'interno della normale attività di rete.
- NDR-302: Vectra AI migliorato la copertura di rilevamento per le comunicazioni TCP in testo semplice, identificando attività di comando sospette nascoste nel traffico non crittografato basato su testo. Questo aggiornamento rileva modelli comportamentali sottili, come flussi di pacchetti anomali e strutture di payload, per scoprire canali di comando nascosti che eludono le ispezioni tradizionali. Espande la visibilità oltre il traffico crittografato, rafforzando il rilevamento su tutti i tipi di comunicazione.
- NDR-314: Vectra AI ampliato la copertura per includere il canale HTTP inglese di Sliver, che maschera il traffico di comando e controllo come stringhe di parole inglesi casuali per apparire legittimo. Questo miglioramento ottimizza il rilevamento delle attività Sliver offuscate all'interno del normale traffico HTTP, rafforzando la visibilità sulle tecniche avanzate di evasione C2.
Chiarezza
Miglioramenti API per CDR per avvisi Azure
Vectra AI introdotto miglioramenti alle API per includere un contesto arricchito leggibile dall'utente (nomi di identità e ID applicazione) nel CDR per gli avvisi Azure consumati tramite API. Questi supportano i flussi di lavoro investigativi riducendo significativamente il tempo richiesto da un analista per raccogliere il contesto chiave. In precedenza, questi valori arricchiti erano disponibili solo nella piattaforma Vectra. I nuovi miglioramenti garantiscono che questi valori siano ora presenti nei flussi di lavoro incentrati sulle API che i clienti potrebbero avere in atto.
Volume di allerta ridotto con triage AI potenziato
AI-Triage di Vectra offre ora funzionalità ampliate lungo tutta la catena di attacco e nelle reti moderne, riducendo significativamente i volumi di rilevamento. Indaga e risolve automaticamente gli avvisi benigni, riducendo l'affaticamento da avvisi e preservando al contempo la piena visibilità sulle minacce reali.
Questa funzionalità personalizzata e rigorosamente testata identifica i modelli a basso rischio che compaiono costantemente nel tuo ambiente e li risolve automaticamente, consentendo al tuo team di concentrarsi sui rischi significativi.
Aspettati meno rilevamenti benigni su rete C2, ricognizione, Azure AD, M365, Copilot per M365 e AWS.
La visibilità non viene mai persa: i rilevamenti risolti rimangono ricercabili, verificabili e completamente tracciabili. Non vengono intraprese azioni per conto dell'utente oltre alla risoluzione.
Grafico degli attacchi: vista focalizzata
Presentiamo Focused View, un nuovo modo per eliminare il rumore dai complessi grafici degli attacchi. Anziché sovraccaricare gli analisti con ogni nodo e ogni bordo, Focused View filtra i rilevamenti a bassa priorità e mostra solo i collegamenti e i percorsi di progressione più critici. Il risultato: meno confusione, meno disordine e una prospettiva chiara su come si è svolto un attacco. Grazie alla chiarezza anziché al disordine, i team di sicurezza possono accelerare le indagini, passando comunque al grafico completo quando necessario.

Data:
Agosto 2025
Rilascio:
9.4
QUX: Interfaccia apparecchiature
JA4+ Impronte digitali
Vectra AI include le impronte digitali JA4L, JA4X e JA4H nei metadati, introducendo il fingerprinting di nuova generazione nell'analisi del traffico crittografato. Questo potente framework riduce le collisioni, collega le sessioni correlate e rende più facile individuare l'infrastruttura degli aggressori nascosta dietro protocolli comuni. Gli analisti ottengono informazioni più chiare e rapide con meno rumore e un contesto migliore tra i rilevamenti. JA4+ è supportato in Investigate (RUX), Stream e Recall. Maggiori informazioni sui nuovi attributi sono disponibili qui.
Avvisi di app esterne (notifiche Webhook)
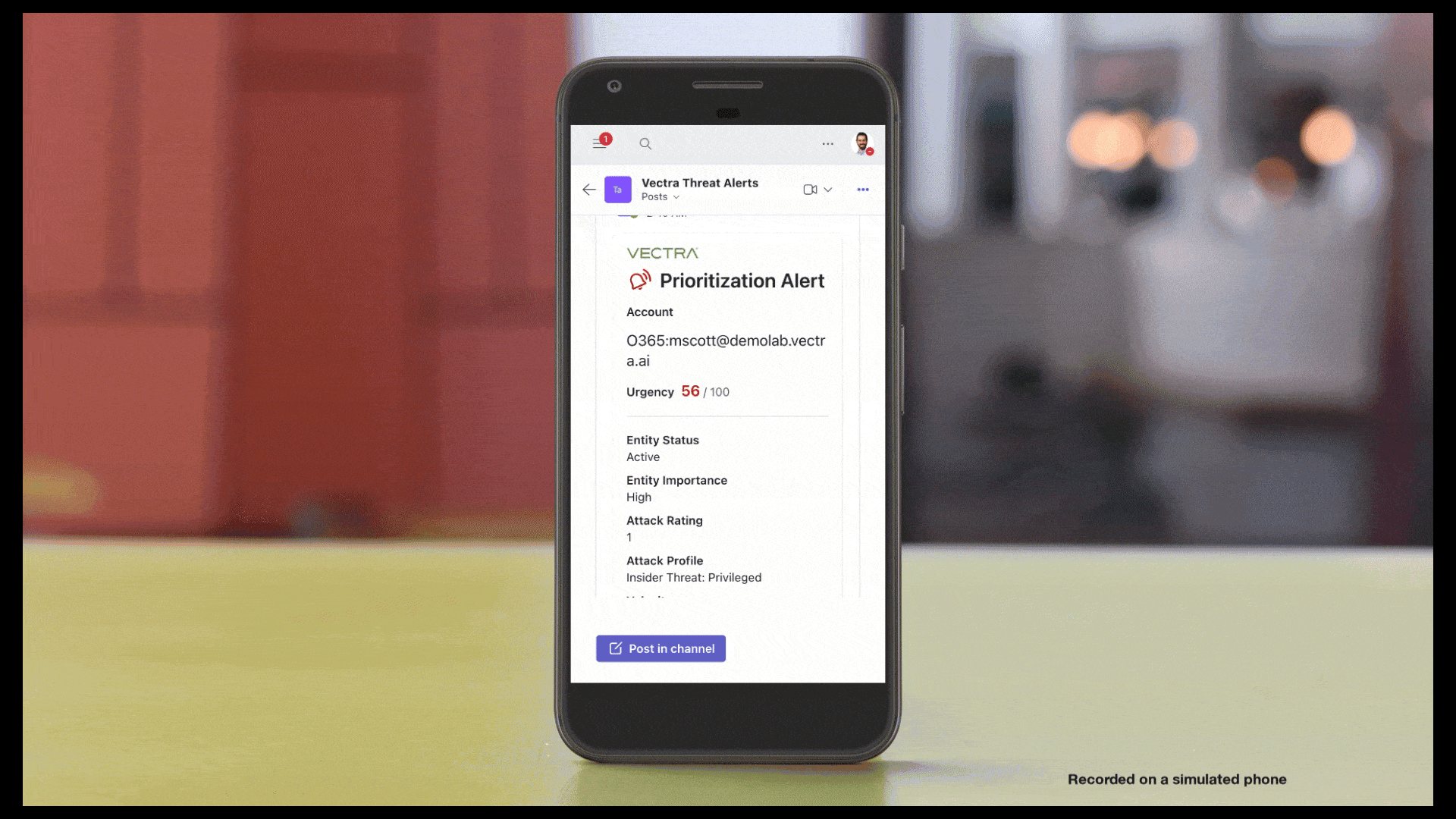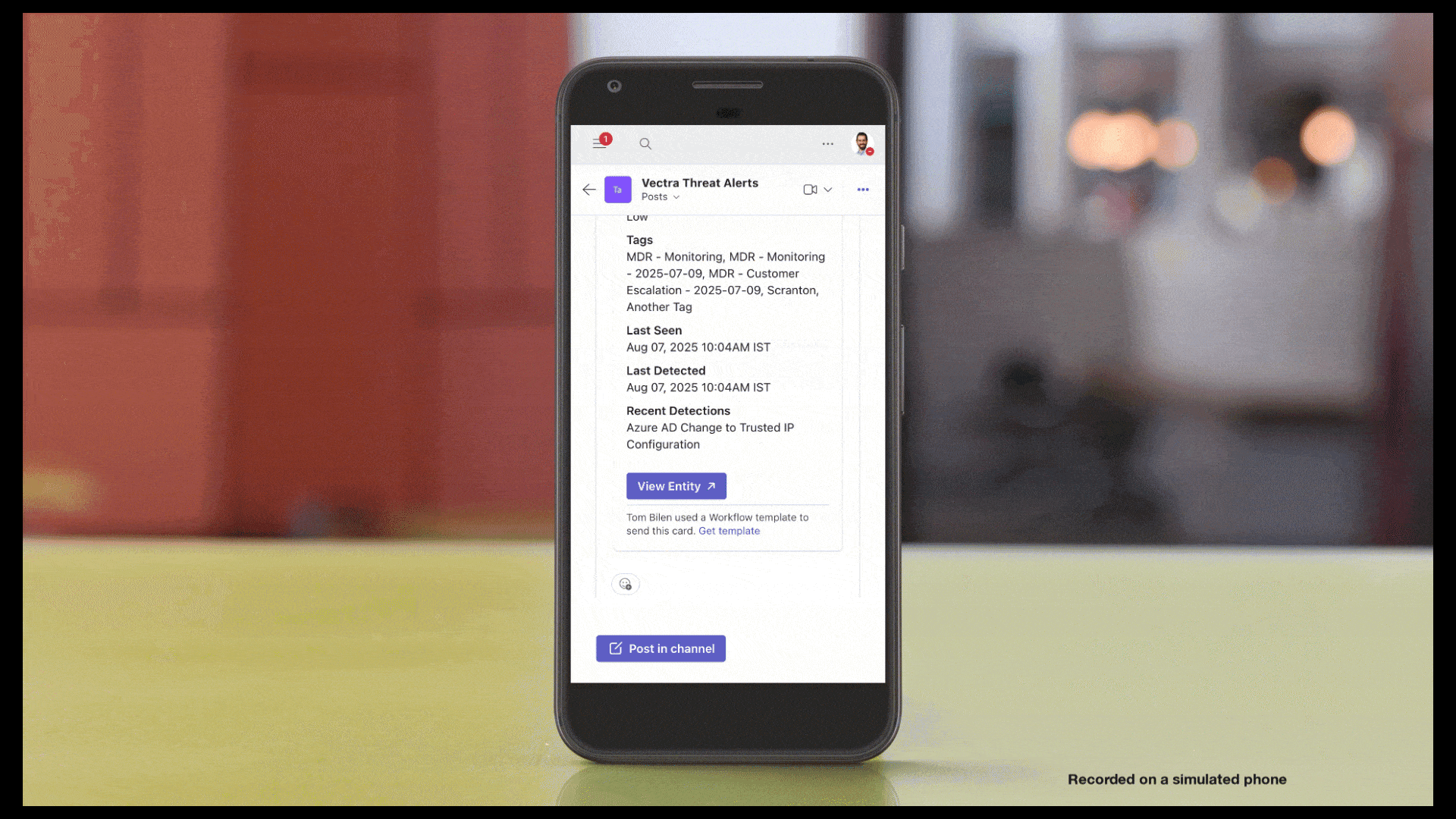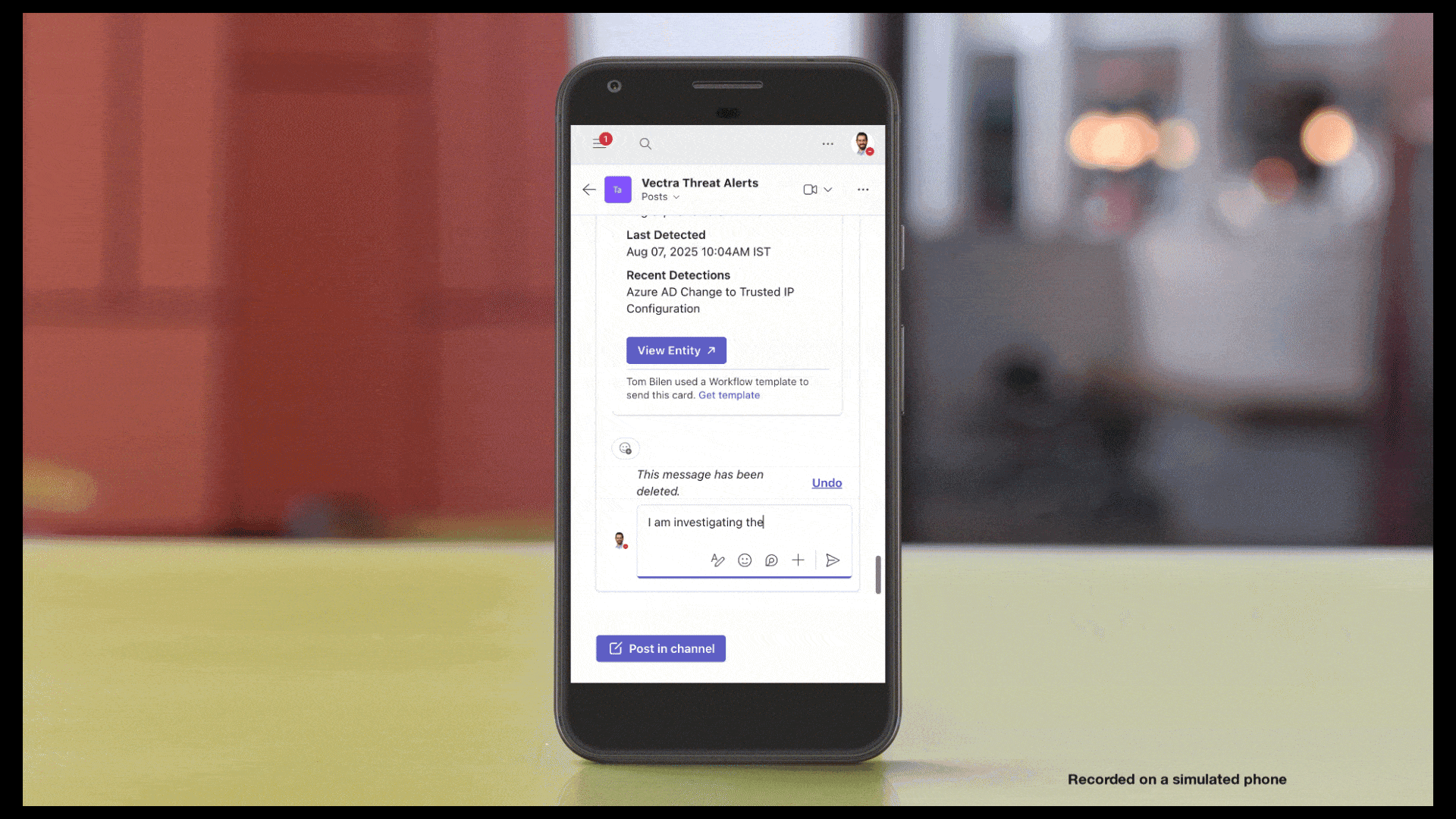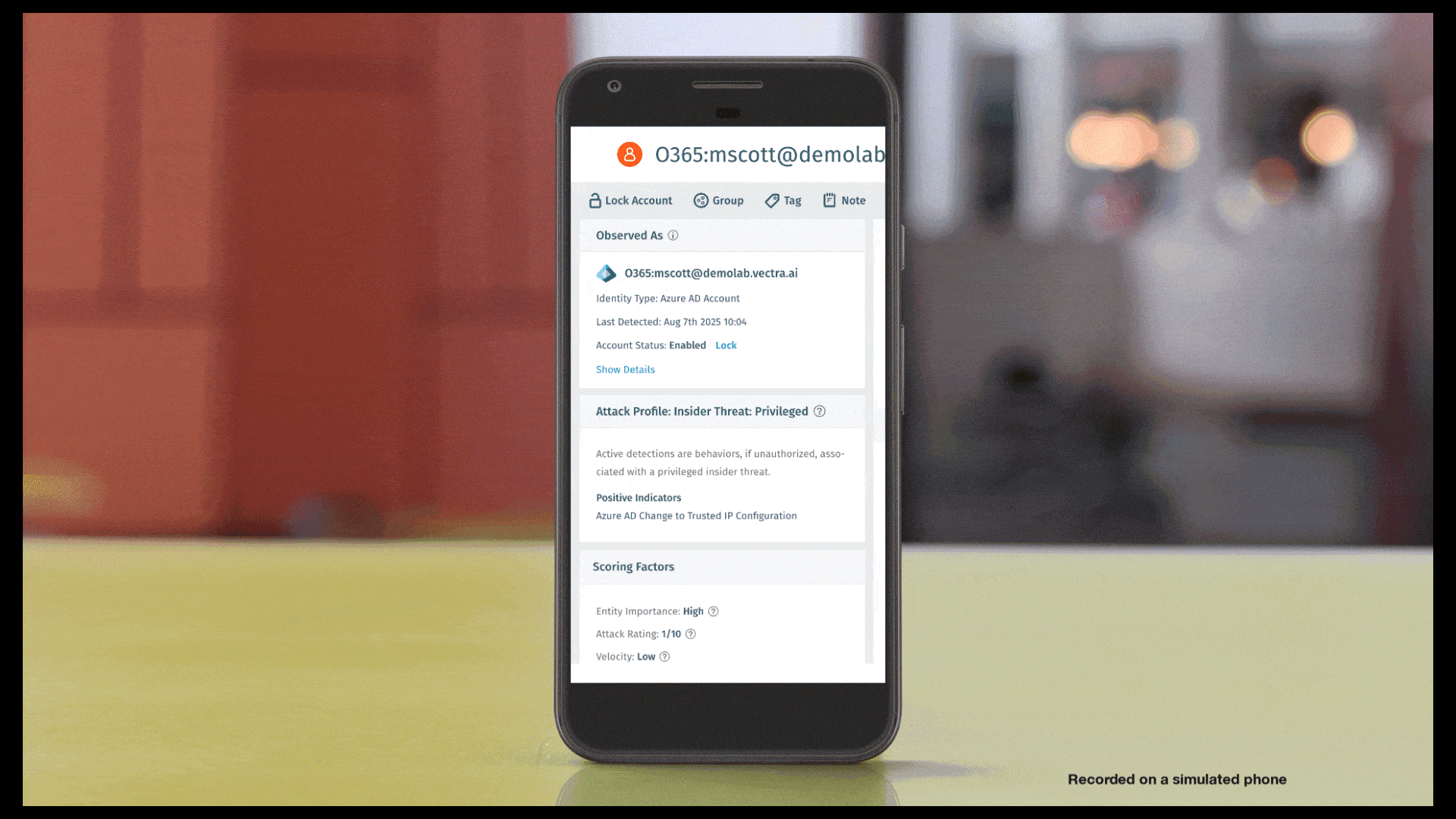
Con gli avvisi delle app esterne, la Vectra AI invia notifiche istantanee agli strumenti di collaborazione del tuo team quando si verificano eventi di sicurezza critici, come host o account ad alta priorità e avvisi di sistema importanti. Non dovrai più stare davanti allo schermo o rispondere in ritardo: riceverai informazioni in tempo reale che ti consentiranno di agire più rapidamente. Disponibile ora con integrazione diretta con Microsoft Teams e supporto Slack in arrivo. Consulta Avvisi delle app esterne per i dettagli sull'implementazione.
Utilizzo del motore di scripting Azure AD
Vectra AI introdotto miglioramenti per ampliare sia la gamma di comportamenti che gli agenti utente coperti da questo rilevamento. Gli aggiornamenti al livello di analisi ora filtrano gli agenti utente in modo più accurato dai log, aumentando la fedeltà e riducendo i falsi positivi.
Miglioramenti dell'interfaccia utente per Entra ID e rilevamenti M365
Sono stati introdotti miglioramenti in diversi sistemi di rilevamento per fornire un contesto aggiuntivo e semplificare i flussi di lavoro investigativi:
- Anomalia delle operazioni privilegiate di Azure AD: ora include i dettagli dell'agente utente, se disponibili.
- Registrazione dei fattori sospetti di Azure AD: aggiornata per includere il campo result_reason dai registri.
- Accesso sospetto ad Azure AD: aggiornato per visualizzare lo stato del dispositivo e migliorare il contesto.
- M365 Spearphishing: aggiornato per visualizzare i nomi dei file, consentendo una selezione più rapida.
Miglioramento del modello Cloud Azure Cloud
I miglioramenti apportati al rilevamento della disabilitazione della registrazione diagnostica di Azure ampliano la copertura per includere l'eliminazione delle estensioni di registrazione sia per le macchine virtuali Windows che Linux. Ciò offre una visibilità più ampia sulle attività sospette che potrebbero indicare tentativi di disabilitare il monitoraggio della sicurezza.
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento Vectra AIcon il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte della versione 9.3:
- NDR-251: aggiunge la copertura di rilevamento per accessi sospetti Mimikatz sul traffico SMB. Ciò migliora la nostra capacità di individuare potenziali tecniche di furto di credenziali comunemente utilizzate negli attacchi.
- NDR-117: amplia la copertura dell'algoritmo di attività amministrativa del protocollo RDP (Remote Desktop Protocol) per una maggiore sicurezza.
- NDR-241: aggiunge una copertura di rilevamento per identificare gli attacchi di forza bruta all'autenticazione NTLM, contribuendo a impedire agli aggressori di violare gli account tramite ripetuti tentativi di accesso.
Data:
Agosto 2025
Rilascio:
9.3
QUX: Interfaccia apparecchiature
Integrazione di Zscaler Internet Access SSE in anteprima pubblica
Vectra AI Zscaler hanno collaborato per eliminare i punti ciechi nelcloud crittografato ecloud . Grazie all'integrazione con Zscaler Internet Access (ZIA), Vectra riproduce il traffico degli utenti da PCAP sicuri per un rilevamento completo delle minacce, scoprendo C2 avanzati ed esfiltrazioni che gli strumenti tradizionali non riescono a individuare. Si tratta di una svolta rivoluzionaria per la sicurezza degli ambienti remoti e cloud. Per ulteriori informazioni, consultare il comunicato stampa e il podcast Vectra AI. Se siete interessati ad abilitare l'integrazione ZIA di Vectra, contattate il vostro team Vectra AI . Per i dettagli sull'implementazione, consultate Zscaler ZIA Integration and Optimization.
Gestione Match delle regole Vectra Match
Vectra Match semplifica il rilevamento degli indicatori di compromissione (IOC) noti con firme compatibili con Suricata, senza bisogno di strumenti esterni. A partire dalla versione 9.3, è possibile gestire, modificare, abilitare o disabilitare le regole direttamente nella piattaforma e le modifiche rimangono anche dopo gli aggiornamenti di Emerging Threats. È più veloce da configurare, più semplice da mantenere e offre il pieno controllo della logica di rilevamento. Per ulteriori informazioni, visitare GestioneMatch Vectra AI Match .
Relazione sintetica per i dirigenti
Vectra AI l'Executive Overview Report, una panoramica sulla sicurezza pronta per essere presentata al consiglio di amministrazione. Progettato appositamente per i CISO e i responsabili della sicurezza, fornisce metriche chiare e di grande impatto, come le tendenze del rapporto segnale/rumore e i modelli di attacco in evoluzione. In pochi minuti avrete a disposizione le informazioni necessarie per dimostrare l'impatto di Vectra, orientare le decisioni strategiche e dimostrare come state riducendo il rischio di violazioni, senza bisogno di approfondimenti.
Visualizzazioni dei grafici degli attacchi in Quadrant UX
Il nuovo Attack Graph offre una visione immediata delle minacce attive, mappando visivamente il modo in cui gli aggressori si muovono all'interno della rete, cloud e degli ambienti di identità. Grazie alla tecnologia Vectra AI , ogni minaccia viene ora visualizzata direttamente sulla pagina dell'host o dell'account, fornendo informazioni immediate sul punto in cui è iniziato l'attacco, sui sistemi con cui ha interagito e sull'evoluzione del suo livello di rischio nel tempo.
I team di sicurezza possono scegliere tra tre visualizzazioni intuitive per indagare sulle minacce nel modo più adatto al loro flusso di lavoro:
- Grafico dell'attacco: scopri come le diverse entità sono collegate durante l'attacco.
- Flusso dell'attacco: osserva la sequenza delle azioni dell'aggressore in un percorso strutturato.
- Cronologia dell'attacco: scopri come è cambiato e si è intensificato il rischio di minaccia.
Questa funzionalità consente ai team SOC di agire rapidamente e con sicurezza, mettendo in evidenza il contesto e l'urgenza in un'unica vista fruibile. Per ulteriori informazioni, consultare le Domande frequenti su Attack Graph.
Impronte digitali JA4/JA4S
Vectra AI include le impronte digitali JA4 e JA4S nei metadati, introducendo il fingerprinting di nuova generazione nell'analisi del traffico crittografato. Questo potente framework riduce le collisioni, collega le sessioni correlate e rende più facile individuare l'infrastruttura degli aggressori nascosta dietro protocolli comuni. Gli analisti ottengono informazioni più chiare e rapide con meno rumore e un contesto migliore tra i rilevamenti. JA4 è supportato in Investigate (RUX), Stream e Recall, con ulteriori funzionalità della suite JA4+ in arrivo. Maggiori informazioni sui nuovi attributi sono disponibili qui.
Interfaccia utente per la convalida del traffico di rete in Quadrant UX
A partire dalla versione 9.3, Vectra AI introdotto nuove pagine di convalida del traffico. Queste pagine trasformano il report JSON di convalida del traffico in un dashboard intuitivo, che mostra le informazioni in modo più rapido e senza la necessità di analizzare i dati grezzi. Le statistiche chiave vengono automaticamente confrontate con soglie di integrità predefinite, con chiari indicatori rossi o gialli che evidenziano le aree che potrebbero richiedere attenzione. Per ulteriori informazioni, consultare le FAQ.
AI-Triage ora risolve automaticamente le minacce più lievi
L'intelligenza artificiale proprietaria Vectra AIè diventata ancora più intelligente. Il nostro algoritmo AI-Triage aggiornato ora indaga e risolve automaticamente il 50% dei rilevamenti C&C benigni e il 25% dei rilevamenti Recon benigni, riducendo drasticamente gli eventi benigni. Sfrutta sia i modelli locali che le informazioni globali per fornire il segnale più chiaro mai ottenuto. Per ulteriori dettagli su AI-Triage, consulta l'articolo e il video su AI-Triage.
Classificazione delle minacce migliorata con la prioritizzazione basata sull'intelligenza artificiale
Vectra AI è stata migliorata per individuare meglio le minacce che rispecchiano i recenti cambiamenti nel comportamento degli aggressori. È prevista una migliore separazione tra minacce elevate e critiche, una prioritizzazione più intelligente in tutto l'ambiente e una prioritizzazione più rapida delle minacce. Si noti che alcuni punteggi di minaccia e certezza di host e account potrebbero variare in base alla logica di punteggio aggiornata una volta aggiornato il sistema.
Migliori pratiche di triage
Vectra AI una nuova serie dedicata alle migliori pratiche, pensata per aiutare gli utenti a sfruttare al meglio le funzionalità chiave della Vectra AI . Il primo articolo di questa serie è dedicato al triage. La guida alle migliori pratiche di triage include la terminologia comune, quando e perché eseguire il triage, istruzioni pratiche, domande frequenti e molto altro ancora. Visita l'articolo sulle migliori pratiche di triage per perfezionare il tuo flusso di lavoro di triage.
Rimozione VirusTotal
Vectra AI rimosso l'integrazione di VirusTotal da Quadrant UX a causa di modifiche alle licenze. Il popup Destinazione esterna non visualizza più i dati di VirusTotal e nella prossima versione è prevista una pulizia completa dell'interfaccia utente per evitare confusione. Per feedback o domande su questa rimozione, contattare il team Vectra AI .
Nuova suite di rilevamento: AWS S3
Vectra AI introdotto tre nuove funzionalità di rilevamento per individuare comportamenti sospetti relativi all'uso di AWS S3 nelle fasi di impatto ed esfiltrazione della catena cloud :
- Eliminazione sospetta di batch S3 AWS: questo rilevamento evidenzia comportamenti associati a download e eliminazioni su larga scala relativi a più file. Questo comportamento può indicare la fase di manipolazione distruttiva dell'attività ransomware nell'ambiente.
- Eliminazione sospetta di oggetti S3 da parte di AWS: analogamente al nuovo rilevamento dell'eliminazione batch da S3, questo rilevamento evidenzia comportamenti in cui singoli oggetti sono stati scaricati e poi eliminati da un bucket S3 in un modo che potrebbe indicare la fase di manipolazione distruttiva dell'attività ransomware nell'ambiente.
- Crittografia S3 sospetta AWS: questo rilevamento evidenzia attività di crittografia insolite che potrebbero indicare una fase di crittografia ransomware in corso. È progettato per rilevare la crittografia di molti oggetti S3 utilizzando una chiave KMS esterna (SSE-KMS) o una chiave controllata dal cliente (SSE-C).
Miglioramenti del segnale per M365, Azure AD e Azure
Sono stati introdotti miglioramenti ai seguenti rilevamenti AAD, Microsoft 365 e Azure per tenere meglio conto del rischio dei comportamenti sottostanti e renderli immediatamente visibili per la revisione. L'introduzione di questi miglioramenti potrebbe comportare modifiche al numero di entità prioritarie all'interno della Vectra AI :
- Attività sospetta di Power Automate in M365: questo rilevamento segnala potenziali comportamenti di esfiltrazione o C2 che utilizzano Power Automate all'interno dell'ambiente. I miglioramenti apportati a questo rilevamento comportano un aumento significativo della sua accuratezza e una riduzione del tasso di falsi positivi osservati in questo rilevamento e in rilevamenti simili (Creazione di flussi HTTP sospetti in Power Automate in M365 e Creazione di flussi sospetti in Power Automate in M365).
- Anomalia delle operazioni con privilegi Azure AD: questo rilevamento segnala operazioni Azure AD anomale potenzialmente associate all'escalation dei privilegi. Vectra AI migliorando questo rilevamento per affinare i comportamenti considerati anomali. Il risultato atteso è una riduzione del rumore relativo a questo rilevamento.
- Operazioni rischiose in Exchange: questo rilevamento segnala operazioni privilegiate all'interno di Exchange che potrebbero essere oggetto di abuso da parte di un aggressore. Vectra AI ampliando l'ambito dei comportamenti presi in considerazione per questo avviso e rimuovendo le azioni potenzialmente innocue in Exchange (come l'impostazione di risposte automatiche). Grazie a questi miglioramenti, i clienti possono aspettarsi una significativa riduzione del volume (oltre il 30%).
- Registrazione diagnostica di Azure disabilitata: questo rilevamento evidenzia comportamenti che compromettono la difesa relativi alla cancellazione delle impostazioni di registrazione diagnostica di Azure. Il rilevamento è stato migliorato per garantire una copertura più ampia in relazione alla cancellazione della registrazione diagnostica sulle macchine virtuali (VM). I clienti potrebbero osservare un leggero aumento dei volumi di rilevamento associati a questo miglioramento.
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento Vectra AIcon il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte della versione 9.3:
- NDR-222: aggiorna il titolo di un rilevamento di attività sospetta del protocollo per un utilizzo sospetto di Windows Remote Management (WinRM). Il nuovo titolo è "Possibile utilizzo dannoso di WinRM" per riflettere meglio la natura del comportamento.
- CS-10426: Risolto un problema che influiva su alcuni rilevamenti di attività sospette del protocollo, in cui gli indirizzi IP di origine e destinazione venivano attribuiti in modo errato a causa del client che fungeva da proxy. Questa correzione è stata applicata a tutti gli algoritmi di rilevamento pertinenti.
- NDR-251: Amplia la copertura di rilevamento contro le tecniche di penetrazione utilizzate dal Kali Linux Package Repository.
- NDR-251: Amplia il rilevamento dell'attività Tor identificando gli IP di destinazione che corrispondono a nodi Tor noti.
Data:
Agosto 2025
Rilascio:
2025.08
RUX: Fornitura SaaS
Contesto più solido con nuovi aggiornamenti al grafico degli attacchi
Vectra AI potenziato l'Attack Graph con due nuove potenti funzionalità. Innanzitutto, gli analisti possono ora visualizzare i rilevamenti che prendono di mira direttamente l'entità oggetto dell'indagine, rendendo più facile rispondere alla domanda: "Come è stata compromessa questa entità?" Ciò consente di individuare rapidamente il "paziente zero" anche in scenari complessi di movimento laterale. In secondo luogo, l'Attack Graph ora visualizza il raggio d'azione dei canali di comando e controllo (C2), espandendosi automaticamente per mostrare tutte le entità collegate allo stesso dominio o IP dannoso. Insieme, questi aggiornamenti accelerano le indagini, rivelano collegamenti nascosti e forniscono ai team un contesto completo per fermare gli attacchi più rapidamente.
Accelerare le indagini con ricerche di cinque minuti
Siamolieti di annunciare che Five Minute Hunts è ora disponibile in Advanced Investigations. Queste ricerche guidate rivelano informazioni significative nei metadati senza richiedere ai clienti di padroneggiare SQL o terminologia specialistica. I team di sicurezza possono scoprire rapidamente i modelli degli aggressori, dimostrare il valore proattivo in "tempi di pace" e aumentare l'efficienza con pochi clic. Dietro le quinte, la funzione è supportata dal nostro framework flessibile di distribuzione dei contenuti, completo di layout adattivi, animazioni fluide e immagini accattivanti per un'esperienza di analisi senza interruzioni.
Avvisi di app esterne (notifiche Webhook)
Con gli avvisi delle app esterne, Vectra AI notifiche istantanee agli strumenti di collaborazione del tuo team quando si verificano eventi di sicurezza critici, come host o account ad alta priorità e avvisi di sistema importanti. Non dovrai più stare davanti allo schermo o attendere risposte ritardate: riceverai informazioni in tempo reale che ti consentiranno di agire più rapidamente. Disponibile ora con integrazione diretta con Microsoft Teams e supporto Slack in arrivo. Consulta Avvisi delle app esterne per i dettagli sull'implementazione.

JA4+ Impronte digitali
Vectra AI include le impronte digitali JA4, JA4S, JA4L, JA4X e JA4H nei metadati, introducendo il fingerprinting di nuova generazione nell'analisi del traffico crittografato. Questo potente framework riduce le collisioni, collega le sessioni correlate e rende più facile individuare l'infrastruttura degli aggressori nascosta dietro protocolli comuni. Gli analisti ottengono informazioni più chiare e rapide con meno rumore e un contesto migliore tra i rilevamenti. JA4+ è supportato in Investigate (RUX), Stream e Recall. Maggiori informazioni sui nuovi attributi sono disponibili qui.
Indagini più semplici con dati CDR Azure leggibili dall'uomo
Vectra AI reso Azure CDR più facile da usare sostituendo gli UUID confusi con nomi chiari e leggibili. I nomi degli account nell'API REST ora riflettono gli ID Entra riconoscibili, mentre l'attività di rilevamento mostra nomi di oggetti e applicazioni intuitivi. Gli analisti non devono più decodificare gli ID grezzi, rendendo più veloce la selezione, più fluide le indagini e più fruibili i dashboard.
Data:
Luglio 2025
Rilascio:
2025.07
RUX: Fornitura SaaS
Gruppi basati sull'appartenenza ad Active Directory
Importa senza problemi i tuoi gruppi AD esistenti in Vectra e mantienili perfettamente sincronizzati, senza più ricreazioni manuali o noiose operazioni di manutenzione. L'importazione in blocco elimina il lavoro amministrativo ripetitivo, consentendo ai tuoi team di concentrarsi sulla ricerca delle minacce, anziché sulla gestione dei gruppi. Ottimizzando le regole di triage e riducendo il rumore, potrai agire più rapidamente sugli avvisi che contano davvero. Si tratta di efficienza e chiarezza del segnale, integrate direttamente. Visita Gruppi Active Directory (AD) per ulteriori informazioni.
Integrazione di Zscaler Internet Access SSE in anteprima pubblica
Vectra AI Zscaler hanno stretto una collaborazione per eliminare i punti ciechi nelcloud crittografato ecloud . Grazie all'integrazione con Zscaler Internet Access (ZIA), Vectra riproduce il traffico degli utenti da PCAP sicuri per un rilevamento completo delle minacce, scoprendo C2 avanzati ed esfiltrazioni che gli strumenti tradizionali non riescono a individuare. Si tratta di una svolta rivoluzionaria per la sicurezza degli ambienti remoti e cloud. Per ulteriori informazioni, consultare il comunicato stampa e il podcast di Vectra. Se siete interessati ad abilitare l'integrazione ZIA di Vectra, contattate il vostro team di account Vectra. Per i dettagli sull'implementazione, consultate Zscaler ZIA Integration and Optimization.
Approfondimenti esecutivi più dettagliati con efficacia del segnale nei rapporti CISO
Vectra AI inserisce le metriche di efficacia dei segnali direttamente nei report CISO, mostrando come i rilevamenti e le entità siano stati risolti come benigni, corretti o non classificati. Questo contesto aggiuntivo dimostra il valore dei rilevamenti più importanti per gli analisti ed evidenzia i risultati delle correzioni a colpo d'occhio. I dirigenti ottengono una chiara visibilità sulla qualità delle minacce, consentendo decisioni di sicurezza più intelligenti e dimostrando il valore misurabile di Vectra.
Visibilità più intelligente con il dashboard di rilevamento della rete
Vectra AI il Network Discovery Dashboard, un nuovo potente strumento che consente di esplorare il proprio ambiente con una mappa di rete interattiva. Gli analisti possono ora tracciare visivamente host e IP, individuare anomalie nel contesto e accelerare le indagini grazie a una navigazione intuitiva. Questo dashboard semplifica gli ambienti complessi, trasformando i dati di rete grezzi in informazioni utili per una risposta alle minacce più rapida e sicura.
Data:
Giugno 2025
Rilascio:
9.2
QUX: Interfaccia apparecchiature
Ampliamento dell'offerta GCP Brain
A partire dalla versione 9.2, Vectra introduce ulteriori offerte Brain ospitate su Google Cloud , o GCP. I nuovi GCP Brain sono in grado di gestire 5 Gb/s e 15 Gb/s e supportano tutte le stesse funzionalità degli altri Cloud Brain.
Aggiunto supporto per gruppi Aggiunto per v2.x. API QUX
A partire dalla versione 9.2, Vectra supporta il recupero dei membri del gruppo endpoint/groups. Per ulteriori informazioni, consultare: https://support.vectra.ai/vectra/article/KB-VS-1638
Triage AI per Cloud su AWS Cloud Azure Cloud
Vectra AI introdotto AI Triage, la sua soluzione proprietaria di intelligenza artificiale agentica, nei suoi portafogli di copertura AWS e Azure. AI-Triage ora indaga automaticamente Cloud AWS Cloud Azure Cloud sulla base di fattori quali la prevalenza e i profili di minaccia, al fine di filtrare le attività innocue negli ambienti dei clienti. L'impatto di AI-Triage è una riduzione delle entità prioritarie e dei corrispondenti carichi di lavoro di indagine per gli analisti SOC.
Attività sospetta del protocollo: rilevamenti interni
Vectra AI ampliando la copertura dei rilevamenti delle attività sospette del protocollo. Ora, le attività sospette del protocollo includono rilevamenti che coprono attacchi laterali interni/ricognizione e supportano i protocolli LDAP, Kerberos, NTLM e SMB. Questa funzione è disattivata per impostazione predefinita, ma può essere abilitata dal cliente ed è inclusa nella linea di prodotti standard Detect. Per ulteriori informazioni su SPA, consultare https://support.vectra.ai/s/article/KB-VS-1793.
Attività sospetta del protocollo: forza bruta
Vectra AI ampliando la copertura dei rilevamenti delle attività sospette del protocollo (SPA). Ora, SPA è in grado di rilevare i tentativi di attacco brute force su tutti i protocolli. Questa regola rileva gli attacchi brute force in cui un aggressore tenta più richieste di autenticazione in un breve periodo di tempo. Gli attacchi brute force possono prendere di mira vari protocolli come SMB, LDAP, FTP, RDP, SSH e HTTP e sono spesso utilizzati dagli avversari per ottenere l'accesso non autorizzato agli account.
Nuovo rilevamento: attività di inoltro NTLM
Vectra AI introdotto un nuovo rilevamento per l'attività di inoltro NTLM. Ciò migliora la visibilità di Vectra sulle tecniche di movimento laterale utilizzate dagli aggressori. Questo rilevamento identifica i tentativi di sfruttare l'autenticazione NTLM osservando quando un aggressore interroga un host e inoltra l'autenticazione acquisita a un altro host, spesso come parte di tentativi di escalation dei privilegi o di compromissione del dominio.
Nuovo rilevamento: individuazione dei dati sensibili con M365 Copilot
Vectra AI introdotto un nuovo rilevamento per individuare comportamenti relativi a M365 CoPilot. Il nuovo rilevamento M365 CoPilot Sensitive Data Discovery individua i casi in cui una sessione CoPilot è stata sfruttata da un'identità per accedere a file che potrebbero contenere informazioni sensibili. Questo rilevamento mira a individuare gli autori delle minacce che utilizzano un account nell'ambiente per scoprire informazioni sensibili.
Nuova suite di rilevamento: AWS Bedrock Detections
Vectra AI introdotto quattro nuove funzionalità di rilevamento per individuare comportamenti sospetti relativi all'uso di AWS Bedrock, un servizio completamente gestito offerto da AWS che semplifica la creazione e l'implementazione di applicazioni di IA generativa.
- Configurazione di registrazione AWS Bedrock disabilitata: questo rilevamento evidenzia i casi in cui è stato osservato che un soggetto ha disabilitato la registrazione dei prompt per AWS Bedrock a livello regionale. La disabilitazione della registrazione dei prompt interrompe l'acquisizione di tutte le attività relative ai prompt e alle risposte nei modelli AWS Bedrock e può indicare un tentativo di compromettere le difese o nascondere un utilizzo dannoso.
- Modello AWS Bedrock abilitato: questo rilevamento identifica attività sospette relative all'abilitazione di un modello AWS Bedrock da parte di un'identità che non ha precedenti di azioni simili. Segnala potenziali accessi non autorizzati a servizi di IA generativa che potrebbero essere sensibili dal punto di vista della sicurezza e associati a costi elevati.
- Attività sospetta su AWS Bedrock: questo rilevamento identifica attività sospette relative all'abilitazione e all'invocazione di un modello AWS Bedrock da parte di un'identità che non ha precedenti di azioni simili. La combinazione di abilitazione e invocazione di un modello suggerisce che un aggressore stia testando e utilizzando il modello, generando risposte a spese della vittima.
- AWS Bedrock Novel Enabled: rileva ogni istanza in cui è abilitato un modello fondamentale AWS Bedrock, poiché questa azione è insolita e può avere implicazioni in termini di costi o sicurezza. Si tratta di un rilevamento informativo che non contribuisce al punteggio o alla prioritizzazione dell'entità. È inteso come un'informazione rilevante per la sicurezza e potrebbe non essere considerato immediatamente sospetto.
Miglioramenti del segnale
Significativa riduzione degli avvisi di priorità benigni grazie ai miglioramenti apportati all'algoritmo di priorità AI di Vectra e agli aggiornamenti di rilevamento. In alcuni casi, i clienti potrebbero riscontrare una riduzione fino al 50% degli avvisi di priorità relativi a host e account, senza compromettere la copertura delle minacce reali.
- Azure AD e M365: gli avvisi di priorità per gli account con rilevamenti specifici sono stati perfezionati, riducendo gli avvisi benigni e mantenendo al contempo il rilevamento degli attacchi moderni. I rilevamenti interessati includono l'attività di download sospetta di M365, che ora incorpora il contesto del numero di sistema autonomo (ASN) e il motore di scripting sospetto di Azure AD, con un'analisi migliorata per l'agente utente.
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte della versione 9.2:
- NDR-166: questa versione migliora il rilevamento dei tunnel DNS ampliando la copertura a tutti i tipi di risposta DNS, fornendo un rilevamento delle minacce più ampio e accurato.
- NDR-144: Migliora il rilevamento C2 contro le tecniche utilizzate dal Covenant C2 Framework.
- NDR-202: questa versione migliora le prestazioni dell'algoritmo alla base dei nostri rilevamenti di exfiltrazione, consentendo un'identificazione più rapida delle minacce.
- NDR-195: Migliora il rilevamento HTTP contro le tecniche di penetrazione utilizzate dal Kali Linux Package Repository.
- NDR-221: Migliora il rilevamento HTTP contro l'uso sospetto di Windows Remote Management (WinRM), rafforzando la visibilità sui potenziali abusi di questo protocollo.
- NDR-232: Migliora il rilevamento delle attività HTTP sospette per tenere conto dell'utilizzo dei proxy, migliorando l'accuratezza del rilevamento negli ambienti con proxy.
Data:
Giugno 2025
Rilascio:
2025.06
RUX: Fornitura SaaS
AI-Triage ora risolve automaticamente le minacce più lievi
L'intelligenza artificiale proprietaria Vectra AIè diventata ancora più intelligente. Il nostro algoritmo AI-Triage aggiornato ora indaga e risolve automaticamente il 50% dei rilevamenti C&C benigni e il 25% dei rilevamenti Recon benigni, riducendo drasticamente gli eventi benigni. Sfrutta sia i modelli locali che le informazioni globali per fornire il segnale più chiaro mai ottenuto. Per ulteriori dettagli su AI-Triage, consulta la KB AI-Triage e il nostro recente video di aggiornamento.
Nuova suite di rilevamento: AWS Bedrock Detections
Vectra AI introdotto quattro nuove funzionalità di rilevamento per individuare comportamenti sospetti relativi all'uso di AWS Bedrock, un servizio completamente gestito offerto da AWS che semplifica la creazione e l'implementazione di applicazioni di IA generativa.
- Configurazione di registrazione AWS Bedrock disabilitata: questo rilevamento evidenzia i casi in cui è stato osservato che un soggetto ha disabilitato la registrazione dei prompt per AWS Bedrock a livello regionale. La disabilitazione della registrazione dei prompt interrompe l'acquisizione di tutte le attività relative ai prompt e alle risposte nei modelli AWS Bedrock e può indicare un tentativo di compromettere le difese o nascondere un utilizzo dannoso.
- Modello AWS Bedrock abilitato: questo rilevamento identifica attività sospette relative all'abilitazione di un modello AWS Bedrock da parte di un'identità che non ha precedenti di azioni simili. Segnala potenziali accessi non autorizzati a servizi di IA generativa che potrebbero essere sensibili dal punto di vista della sicurezza e associati a costi elevati.
- Attività sospetta su AWS Bedrock: questo rilevamento identifica attività sospette relative all'abilitazione e all'invocazione di un modello AWS Bedrock da parte di un'identità che non ha precedenti di azioni simili. La combinazione di abilitazione e invocazione di un modello suggerisce che un aggressore stia testando e utilizzando il modello, generando risposte a spese della vittima.
- AWS Bedrock Novel Enabled: rileva ogni istanza in cui è abilitato un modello fondamentale AWS Bedrock, poiché questa azione è insolita e può avere implicazioni in termini di costi o sicurezza. Si tratta di un rilevamento informativo che non contribuisce al punteggio o alla prioritizzazione dell'entità. È inteso come un'informazione rilevante per la sicurezza e potrebbe non essere considerato immediatamente sospetto.
Nuova suite di rilevamento: AWS S3
Vectra AI introdotto tre nuove funzionalità di rilevamento per individuare comportamenti sospetti relativi all'uso di AWS S3 nelle fasi di impatto ed esfiltrazione della catena cloud :
- Eliminazione sospetta di batch S3 AWS: questo rilevamento evidenzia comportamenti associati a download e eliminazioni su larga scala relativi a più file. Questo comportamento può indicare la fase di manipolazione distruttiva dell'attività ransomware nell'ambiente.
- Eliminazione sospetta di oggetti S3 da parte di AWS: analogamente al nuovo rilevamento dell'eliminazione batch da S3, questo rilevamento evidenzia comportamenti in cui singoli oggetti sono stati scaricati e poi eliminati da un bucket S3 in un modo che potrebbe indicare la fase di manipolazione distruttiva dell'attività ransomware nell'ambiente.
- Crittografia S3 sospetta AWS: questo rilevamento evidenzia attività di crittografia insolite che potrebbero indicare una fase di crittografia ransomware in corso. È progettato per rilevare la crittografia di molti oggetti S3 utilizzando una chiave KMS esterna (SSE-KMS) o una chiave controllata dal client (SSE-C).
Abilitazione CDR Azure senza soluzione di continuità
Vectra AI semplificato l'abilitazione di Azure CDR con una nuova correzione del servizio Redirector. I clienti possono ora implementare Azure CDR senza problemi, senza che VPN o restrizioni IP ne blocchino la configurazione. Ciò elimina gli attriti nell'integrazione cloud , garantendo un time-to-value più rapido e una visibilità immediata delle minacce Azure. I team di sicurezza ottengono una copertura più rapida con meno complicazioni.
Gestione Match delle regole Vectra Match
Vectra Match semplifica il rilevamento degli indicatori di compromissione (IOC) noti con firme compatibili con Suricata, senza bisogno di strumenti esterni. A partire dalla versione 9.3, è possibile gestire, modificare, abilitare o disabilitare le regole direttamente nella piattaforma e le modifiche rimangono anche dopo gli aggiornamenti di Emerging Threats. È più veloce da configurare, più semplice da mantenere e offre il pieno controllo della logica di rilevamento. Per ulteriori informazioni, visitare Gestione Match di Vectra Match .
Data:
Maggio 2025
Rilascio:
2025.05
RUX: Fornitura SaaS
Presentazione: Rapporto di sintesi esecutivo
Vectra presenta il rapporto Executive Overview sulla Vectra AI . Questo rapporto è rivolto ai CISO e ai responsabili della sicurezza che devono presentare metriche di alto livello alle riunioni del consiglio di amministrazione o dei dirigenti. Le metriche includono il rapporto rumore/segnale, il tempo risparmiato nelle indagini grazie a Vectra, le tendenze degli attacchi e altro ancora. Questo rapporto consente ai dirigenti di prendere decisioni strategiche e valutare in che modo Vectra riduce il rischio di violazioni della sicurezza per la loro organizzazione.
Presentazione: Global View
Global View consente alle grandi imprese e agli MSSP di gestire e analizzare centralmente le minacce su più Brains e tenant da un'unica implementazione RUX, rendendolo ideale per operazioni globali con ambienti complessi.
Presentazione: Grafici di attacco
Il nuovo Attack Graph offre una visione immediata delle minacce attive, mappando visivamente il modo in cui gli aggressori si muovono all'interno della rete, cloud e degli ambienti di identità. Grazie alla tecnologia di prioritizzazione basata sull'intelligenza artificiale di Vectra, ogni minaccia viene ora visualizzata direttamente sulla pagina dell'host o dell'account, fornendo informazioni immediate sul punto di origine dell'attacco, sui sistemi con cui ha interagito e sull'evoluzione del suo livello di rischio nel tempo.
I team di sicurezza possono scegliere tra tre visualizzazioni intuitive per indagare sulle minacce nel modo più adatto al loro flusso di lavoro:
- Grafico di connettività: mostra come le diverse entità sono collegate durante l'attacco.
- Grafico ad albero: visualizza la sequenza delle azioni dell'autore dell'attacco in un percorso strutturato.
- Punteggio storico nel tempo: comprendi come il rischio della minaccia è cambiato e aumentato.
Questa funzionalità consente ai team SOC di agire rapidamente e con sicurezza, mettendo in evidenza il contesto e l'urgenza in un'unica vista fruibile.
Scarica il rapporto di convalida del traffico Problema risolto
Abbiamo risolto un problema che impediva ad alcuni clienti, in particolare quelli con ambienti RUX di grandi dimensioni, di scaricare il rapporto di convalida del traffico di rete quando la sua dimensione superava i 6 MB circa. Il flusso di lavoro è stato migliorato per supportare il download di rapporti più grandi, garantendo un accesso affidabile ai dati di convalida del traffico indipendentemente dalle dimensioni del rapporto.
Data:
Maggio 2025
Rilascio:
9.1
QUX: Interfaccia apparecchiature
Introduzione al sistema di rete Vectra X47/M47
A partire dalla versione 9.1, Vectra introduce i nuovi sistemi X47 e M47. Come gli altri sistemi della serie X, l'X47 può essere implementato in modalità Brain, Sensor o Mixed. L'M47 supporta Vectra Stream velocità fino a 75 Gbps. L'hardware è dotato di 4 porte in rame da 1 Gbps e 2 porte SFP28 da 10/25 Gbps. Per ulteriori informazioni sulle specifiche dell'apparecchio, consultare le Specifiche dell'apparecchio e del sensore.
Per le guide all'implementazione, consultare la Guida rapida X47 o la Guida rapida M47.
Modifica del tipo di gruppo su Quadrant UX Network
A partire dalla versione 9.1, Vectra supporta la conversione tra tipi di gruppi statici e dinamici per le distribuzioni QUX. I filtri di triage esistenti che fanno riferimento a un gruppo statico continueranno a funzionare senza richiedere alcuna modifica dopo che il gruppo è stato ridefinito utilizzando un'espressione regolare nella configurazione del gruppo dinamico. Ciò dovrebbe consentire una maggiore flessibilità e facilità di implementazione man mano che i clienti passano ai gruppi dinamici. Per ulteriori informazioni sui gruppi dinamici, consultare le Domande frequenti sui gruppi dinamici.
Miglioramenti nella gestione delle chiavi SSL
A partire dalla versione 9.1, Vectra AI supporta Vectra AI i certificati ECC (Elliptic Curve Cryptography). I clienti possono caricare il proprio certificato tramite i comandi esistenti. Inoltre, sono stati aggiornati i comandi che supportano la richiesta di firma del certificato (CSR). Utilizzo:
- `certificate replace-key` per generare una nuova chiave e un certificato autofirmato da utilizzare per il server HTTPS, ripristinando essenzialmente le impostazioni predefinite ma consentendo al cliente di personalizzare la lunghezza della chiave.
- `certificate info` per stampare alcune informazioni sul certificato HTTPS corrente affinché l'utente possa visualizzarle.
Per i dettagli completi sull'installazione del certificato, consultare: Installazione del certificato SSL (solo Quadrant UX).
Aggiornamento versione Vectra Match
Vectra AI aggiornato Suricata per supportare nuove funzionalità nel motore Suricata, tra cui JA4, e abbiamo abilitato l'analisi dei protocolli OT. Anche la configurazione di base suricata.yaml è stata aggiornata per riflettere le ultime funzionalità di Suricata. Per ulteriori dettagli sulla configurazione Suricata di Vectra, consultare: Configurazione Match di Vectra Match .
Aggiunto supporto Oauth2 per v2.x. API QUX
Vectra ai ha aggiornato le API QUX v2.x per includere il supporto per l'autenticazione OAuh2. Ora, sia il Personal Access Token (PAT) esistente che il flusso Oauth2 sono supportati nella v2.x. Il token di accesso Oauth2 sarà valido per 6 ore, dopodiché scadrà e sarà necessario richiedere un nuovo token utilizzando le credenziali del client API. La creazione del client API deve essere effettuata esclusivamente nell'interfaccia utente di Vectra. L'accesso alle API v2.x precedenti alla v2.5 funziona allo stesso modo della v2.5. La raccolta pubblica di Postman è stata aggiornata per tutte le versioni v2.x. Per ulteriori informazioni, consultare: Guida rapida all'API REST per Postman v2.5 utilizzando OAuth2 (QUX).
Miglioramento del rilevamento dei tunnel nascosti
Il rilevamento dei tunnel nascosti è stato migliorato per identificare nuove connessioni senza beacon che stanno contattando sistemi esterni. Questo miglioramento fornisce una nuova copertura per gli strumenti di attacco senza beacon basati sulla riga di comando dei tunnel nascosti. Per ulteriori informazioni sul rilevamento dei tunnel nascosti in generale, consultare Informazioni Vectra AI .
Miglioramento del rilevamento RDP Recon
Il rilevamento RDP Recon è stato migliorato per rilevare gli attacchi RDP Password Spray, con cui un aggressore può tentare di testare un numero limitato di password su un numero elevato di account. La versione precedente di RDP Recon si concentrava su un aggressore che tentava di provare un numero elevato di password su un account, mentre questo miglioramento estende RDP Recon per coprire scenari in cui viene condotto un attacco brute force molto superficiale su molti account.
Miglioramenti al rilevamento AWS AWS
Sono stati introdotti miglioramenti alle seguenti rilevazioni AWS per aumentarne l'accuratezza. L'introduzione di questi miglioramenti comporta una copertura più ampia dei comportamenti dannosi e può essere associata a lievi aumenti delle entità prioritarie all'interno degli ambienti dei clienti.
- AWS Cryptomining: questo rilevamento segnala comportamenti relativi all'avvio di più istanze di calcolo ad alta potenza. È stato ampliato per rilevare una gamma più ampia di attività di cryptomining attribuite sia a soggetti umani che non umani. I clienti potrebbero osservare un leggero aumento del volume dei rilevamenti.
- Strumenti di attacco AWS: questo rilevamento segnala gli strumenti di attacco noti in un ambiente AWS. È stato migliorato per garantire una maggiore fedeltà e un tasso di falsi positivi inferiore.
Miglioramenti del segnale
Significativa riduzione degli avvisi di priorità benigni grazie ai miglioramenti apportati all'algoritmo di priorità AI di Vectra e agli aggiornamenti di rilevamento. In alcuni casi, i clienti potrebbero riscontrare una riduzione fino al 50% degli avvisi di priorità relativi a host e account, senza compromettere la copertura delle minacce reali.
- Azure AD e M365: gli avvisi di priorità per gli account con rilevamenti specifici sono stati perfezionati, riducendo gli avvisi benigni e mantenendo al contempo il rilevamento degli attacchi moderni. I rilevamenti interessati includono attività di dirottamento DLL M365, accesso sospetto Azure AD da Cloud e accesso sospetto Azure AD.
- Rete: gli avvisi di priorità per gli host con rilevamenti specifici sono stati perfezionati, riducendo gli avvisi benigni e mantenendo al contempo il rilevamento degli attacchi moderni. I rilevamenti interessati includono modelli quali attività amministrative sospette e co-occorrenze di scansione delle porte, scansione della darknet e port sweep.
Miglioramenti al rilascio rapido
Dall'ultimo ciclo di rilascio del software sono stati apportati i seguenti miglioramenti agli algoritmi. I clienti connessi al servizio di aggiornamento di Vectra con il supporto remoto abilitato hanno già ricevuto questi miglioramenti. Tutti gli altri clienti riceveranno i seguenti miglioramenti come parte della versione 9.1:
- NDR-96: questa versione introduce un miglioramento al nostro algoritmo RDP Recon, ampliando la copertura degli attacchi RDP Sweep in cui sono presenti misure di evasione per limitare il numero di password tentate per account.
- NDR-106: Migliora i nostri rilevamenti C2 contro le tecniche utilizzate da Mythic C2.
- NDR-104: questa versione introduce la copertura degli attacchi per l'exploit Apache Camel Case: CVE-2025–27636.
- NDR-73: questa versione introduce un miglioramento del segnale di attacco per l'accesso remoto esterno al fine di ridurre i rilevamenti benigni veri positivi verso destinazioni popolari.
- NDR-108: questa versione introduce un miglioramento per aumentare la scalabilità e l'integrità del Beacon Detector in condizioni di carico elevato, limitando i metadati dei beacon per le destinazioni benigne più diffuse nell'ambiente.
Data:
Aprile 2025
Rilascio:
2025.04
RUX: Fornitura SaaS
Ricerca migliorata per nome del sensore
Abbiamo migliorato la funzionalità di ricerca nella pagina Rilevamenti per supportare la ricerca per nome del sensore invece che per LUID interno del sensore. Questo aggiornamento risponde al feedback dei clienti e semplifica la ricerca dei rilevamenti associati a sensori specifici utilizzando nomi riconoscibili.
Rilevamento avanzato degli abusi da parte dei copiloti in M365
In risposta al forte interesse dei clienti, stiamo ampliando la protezione contro potenziali abusi di Microsoft Copilot. Oltre all'attuale rilevamento M365 Suspicious Copilot Access (che segnala gli accessi da posizioni insolite), stiamo introducendo un nuovo rilevamento: M365 Copilot Sensitive Data Discovery. Questo identifica il comportamento degli aggressori che tentano di individuare documenti sensibili tramite Copilot in Microsoft 365.
Data:
Marzo 2025
Rilascio:
2025.03
RUX: Fornitura SaaS
Arricchimento del contesto di prioritizzazione dell'IA
Vectra ora mostra profili di attacco personalizzati quando i rilevamenti coprono più superfici di attacco, aiutando a identificare minacce complesse con maggiore chiarezza. Sono stati introdotti due nuovi tipi di profilo:
- Avversario di rete ibrida: indica un aggressore attivo sia negli ambienti di identità di rete che in quelli cloud , suggerendo un'attività coordinata tra cloud locali e cloud .
- AvversarioCloud : rappresenta un aggressore che opera su più servizi cloud, come provider di identità, piattaforme SaaS o cloud pubblici, senza interagire direttamente con i sistemi di identità di rete.
Questi profili sono progettati per riflettere la natura delle minacce ibride e migliorare il contesto delle minacce nell'interfaccia utente.
Supporta il triage AI per le rilevazioni di Azure
Vectra sta migliorando il supporto per i rilevamenti Azure abilitando AI Triage per gli avvisi Azure CDR (Cloud and Response). Per ogni tipo di rilevamento Azure esistente, stiamo valutando e applicando algoritmi di distillazione AI appropriati, definendo campi contestuali rilevanti e affrontando eventuali requisiti di gestione specifici. Ciò contribuirà a far emergere informazioni altamente affidabili in modo più efficiente e a migliorare la chiarezza dei rilevamenti all'interno della piattaforma.
Data:
Marzo 2025
Rilascio:
9.0
QUX: Interfaccia apparecchiature
Introduzione dei gruppi dinamici su Quadrant
A partire dalla versione 9.0, Vectra AI supporta Vectra AI i gruppi dinamici su Quadrant UX. I gruppi dinamici sono una funzionalità della Vectra AI che consente ai clienti di utilizzare regole Regex per definire quali host o account devono appartenere a ciascun gruppo di triage, con il risultato che le entità vengono automaticamente ordinate in gruppi man mano che vengono rilevate. Questa funzionalità ridurrà il tempo che i clienti dedicano alla gestione e all'aggiornamento dei gruppi. Il supporto di Respond UX per questa funzionalità è stato introdotto nel dicembre 2024. Per ulteriori informazioni, consultare: https://support.vectra.ai/s/article/KB-VS-1839.
Rete GCP Brains ad alte prestazioni
Vectra ai ha creato una nuova variante a 64 core del GCP Brain e ha convalidato il Brain a 96 core esistente per supportare un throughput complessivo superiore rispetto a quello pubblicato in precedenza. Per ulteriori dettagli, consultare la Guida all'implementazione del GCP Brain.
Supporto proxy per attività sospette del protocollo e Match
A partire dalla versione 9.0, Vectra AI il supporto proxy automatico per Match SPA. Sebbene non sia richiesta alcuna azione da parte dell'utente, Match disponibili variabili aggiuntive per Match . Per ulteriori dettagli, consultare le Match : https://support.vectra.ai/s/article/KB-VS-1635.
IP proxy Southside tramite CLI
A partire dalla versione 9.0, Vectra ha aggiunto il supporto per visualizzare gli IP proxy dell'elenco appreso southside tramite riga di comando. I proxy southside identificano i proxy in cui Vectra si trova tra il client e il proxy. Ciò differisce dai proxy northside che sono configurati in Gestisci -> Proxy nell'interfaccia utente. Utilizzare "show proxy --southside" per visualizzare i proxy southside che il sistema ha appreso osservando il traffico di rete.
Rapporto di convalida del traffico migliorato
A partire dalla versione 9.0, Vectra AI aggiunto nuovi campi al report Enhanced Network Traffic Validation (Convalida avanzata del traffico di rete) disponibile nella pagina Network Stats (Statistiche di rete). I nuovi campi includono statistiche su errori NIC, troncamento dei pacchetti e perdite/interruzioni nel traffico. Per ulteriori informazioni, consultare: https://support.vectra.ais/article/KB-VS-1648.
Interfacce S1 SFP+ supportate per MGT1 o utilizzo Capture
Starting in 9.0, Vectra now supports the use of the S1’s two onboard SFP+ interfaces for capture or management. The command “set management <default|sfp>” will alter the interface configuration for the MGT1 port. The command “set capture <default|sfp>” will alter the interface assignment used for capture. This creates 4 total configurations for management or capture. All options with new interface assignment diagrams for each are detailed in the S1 Quick Start Guide. Please note: The rated throughput of the S1 appliance does not change when using SFP+ ports. This only changes the physical interface assignments. Care should be taken to only forward a supported amount of traffic to the S1.
Appliance X29/M29 – Nuova sintassi per l'utilizzo di SFP+ per MGT
The X29/M29 appliances have an option to configure one of their SFP+ interfaces to be used as the MGT1 management port. The command has changed in version 9.0 to be consistent with the command syntax that is used now for all appliances that offer options to change similar interface options. The old command was “set management speed <1G|10G>” and the new command is “set management <default|sfp>”. Please see the X29 Quick Start Guide or the M29 Quick Start Guide for details.
Miglioramenti alle rilevazioni AWS
Sono stati introdotti miglioramenti alle seguenti rilevazioni AWS per aumentarne l'accuratezza. L'introduzione di questi miglioramenti comporta una copertura più ampia dei comportamenti dannosi e può essere associata a lievi aumenti delle entità prioritarie all'interno degli ambienti dei clienti.
- Registrazione AWS CloudTrail disabilitata: questo rilevamento avvisa della tecnica di elusione della difesa che consiste nel disattivare la registrazione AWS. Sono stati introdotti miglioramenti al modello per ampliare il profilo comportamentale che rappresenta questo comportamento dannoso.
- Modifica della registrazione AWS CloudTrail: questo rilevamento segnala la tecnica di elusione della difesa che consiste nel downgrade della registrazione AWS. Sono stati introdotti miglioramenti al modello per ampliare il profilo comportamentale che rappresenta questo comportamento dannoso.
- Dirottamento utente AWS: questo rilevamento segnala le tecniche di persistenza relative alla creazione di chiavi di accesso AWS. In questo modello è stato introdotto un ulteriore apprendimento per tenere conto del ripetersi di determinati comportamenti e del conseguente impatto sul volume degli avvisi generati. Questo miglioramento comporta una maggiore efficacia degli avvisi relativi a questo comportamento rischioso.
Miglioramenti al punteggio dei rilevamenti M365
Sono stati introdotti miglioramenti ai seguenti rilevamenti di Microsoft 365 per tenere meglio conto del rischio dei comportamenti sottostanti e renderli immediatamente visibili per la revisione. L'introduzione di questi miglioramenti potrebbe comportare modifiche al numero di entità prioritarie all'interno della piattaforma Vectra:
- Attività sospetta di Power Automate in M365: questo rilevamento segnala potenziali comportamenti di esfiltrazione o C2 che utilizzano Power Automate all'interno dell'ambiente. I miglioramenti apportati a questo rilevamento comportano un aumento significativo della sua accuratezza e una riduzione del tasso di falsi positivi osservati in questo rilevamento e in rilevamenti simili (Creazione di flussi HTTP sospetti in Power Automate in M365 e Creazione di flussi sospetti in Power Automate in M365).
Data:
Febbraio 2025
Rilascio:
2025.02
RUX: Fornitura SaaS
Fornire supporto per l'autenticazione tramite OAuth
Vectra supporta sia il token di accesso personale (PAT) esistente che il flusso Oauth2 nella versione v2.x. Il token di accesso Oauth2 sarà valido per 6 ore, dopodiché scadrà e sarà necessario richiedere un nuovo token utilizzando le credenziali del client API. La creazione del client API deve essere effettuata esclusivamente nell'interfaccia utente di Vectra. L'accesso alle API v2.x precedenti alla v2.5 funziona allo stesso modo della v2.5. La raccolta pubblica di Postman è stata aggiornata per tutte le versioni v2.x.
Supporto M365 GCC
Vectra ora supporta gli ambienti Microsoft 365 Government Community Cloud GCC). Sebbene in precedenza fosse già previsto il supporto per i clienti GCC-High e Azure AD, questo aggiornamento estende la copertura ai clienti che operano in ambienti GCC, comunemente utilizzati dalle agenzie statali, locali e federali degli Stati Uniti. Grazie all'integrazione con gli endpoint specifici GCC di Microsoft, Vectra AI un'aggregazione dei log sicura e conforme, fornendo visibilità completa e rilevamento delle minacce su tutti cloud governativo Microsoft.
Assistenza Cybereason EDR
Vectra ha aggiunto il supporto per l'acquisizione degli avvisi EDR da Cybereason. I clienti che utilizzano Cybereason possono ora configurare la loro integrazione all'interno di Cantina per abilitare l'acquisizione e la visibilità degli avvisi.
Modifica del tipo di gruppo
A partire dalla versione 9.1, Vectra supporta la conversione tra tipi di gruppi statici e dinamici per le distribuzioni QUX. I filtri di triage esistenti che fanno riferimento a un gruppo statico continueranno a funzionare senza richiedere alcuna modifica dopo che il gruppo è stato ridefinito utilizzando un'espressione regolare nella configurazione del gruppo dinamico. Ciò dovrebbe consentire una maggiore flessibilità e facilità di implementazione man mano che i clienti passano ai gruppi dinamici. Per ulteriori informazioni sui gruppi dinamici, consultare le Domande frequenti sui gruppi dinamici.
Data:
Gennaio 2025
Rilascio:
2025.01
RUX: Fornitura SaaS
Supporto Disabilitazione rilevamento DNS
Gli utenti possono ora disabilitare l'ispezione dei pacchetti di risposta DNS nella pagina Impostazioni. Se selezionata, verrà visualizzato un messaggio di avviso per informare gli utenti che la disabilitazione della registrazione dei pacchetti di risposta DNS potrebbe influire sui rilevamenti correlati.
Indaga da qualsiasi luogo: IP dell'ultimo accesso
Gli utenti possono ora passare alle indagini avanzate da punti dati chiave al di fuori della pagina Indagini avanzate. Questo aggiornamento introduce un nuovo menu nel campo IP visto l'ultima volta all'interno delle schede Host nella pagina Rispondi. Passando con il mouse sul campo IP visto l'ultima volta, gli utenti possono selezionare una query contenente l'indirizzo IP e passare direttamente ai risultati della query nella pagina Indagini avanzate.
Navigazione principale migliorata
Per supportare il numero crescente di dashboard, la navigazione è stata aggiornata passando dalle schede orizzontali a una barra laterale verticale comprimibile. Questa riprogettazione offre agli utenti un modo più scalabile e intuitivo per accedere e gestire le dashboard.
Miglioramenti alla riconciliazione dei conti federati
Questo aggiornamento aggiunge il supporto per la riconciliazione degli account federati in EntraID con i relativi nomi principali utente (UPN), compreso l'allineamento con le entità CDR di Azure corrispondenti e gli account M365/AzureAD.
Data:
Gennaio 2025
Rilascio:
8.10
QUX: Interfaccia apparecchiature
Miglioramenti relativi ai tempi di inattività del backup
A partire dalla versione 8.10, Vectra ha migliorato i tempi di inattività del backup, che ora richiede meno di dieci minuti per essere completato. L'usabilità della funzione di backup rimane invariata, ma questa soluzione introduce una drastica riduzione dei tempi di completamento dei backup.
Nuovo vSensor VMWare
A partire dalla versione 8.10, Vectra aumenterà la capacità di larghezza di banda dei sensori VMWare vSensors. I sensori VMWare sono in grado di gestire 20 Gb/s di traffico e supportano tutte le stesse funzionalità degli altri sensori Cloud. Per ulteriori informazioni, consultare la nostra guida all'implementazione: https://support.vectra.ai/s/article/KB-VS-1075
Tunnel DNS nascosto Miglioramento NoReply
Nell'ambito della versione 8.10, Vectra ha migliorato il rilevamento dei tunnel DNS nascosti per individuare i casi in cui un aggressore potrebbe tentare di sottrarre dati tramite DNS utilizzando tecniche in cui il server non risponde (pertanto il tunnel è solo un tunnel unidirezionale in cui l'aggressore trasmette i dati dall'interno verso l'esterno).
Miglioramenti al punteggio dei rilevamenti di Azure AD e M365
Sono stati introdotti miglioramenti ai seguenti rilevamenti di Microsoft 365 e Azure AD per tenere meglio conto del rischio dei comportamenti sottostanti e renderli immediatamente visibili per la revisione. L'introduzione di questi miglioramenti potrebbe comportare modifiche al numero di entità prioritarie all'interno della piattaforma Vectra:
- Azure AD/Entra ID
- Impostazioni dominio Azure AD modificate: questo rilevamento avvisa quando un nuovo dominio non verificato o verificato viene aggiunto in modo sospetto all'ambiente.
- Modifica dell'accesso cross-tenant di Azure AD: questo rilevamento genera un avviso quando vengono aggiunte o aggiornate le impostazioni di accesso cross-tenant di un partner.
- Nuova autorità di certificazione Azure AD registrata: questo rilevamento avvisa quando una nuova autorità di certificazione viene registrata nel tenant.
- Anomalia delle operazioni con privilegi Azure AD: questo rilevamento avvisa in caso di potenziali comportamenti di escalation dei privilegi o appropriazione indebita di account all'interno dell'ambiente. I miglioramenti apportati a questo rilevamento comportano un aumento significativo della sua accuratezza e una riduzione del tasso di falsi positivi.
- Microsoft 365
- Modifica della configurazione Phishing M365: questo rilevamento avvisa quando viene modificata la configurazione associata a un Phishing .
Modifica della casella di posta SecOps M365: questo rilevamento avvisa quando viene modificata la configurazione associata a un account SecOps.
Data:
Dicembre 2024
Rilascio:
2024.12
RUX: Fornitura SaaS
Lancio di CDR per Azure
Vectra AI rilevamenti basati sull'intelligenza artificiale che smascherano i comportamenti degli aggressori che prendono di mira cloud Microsoft Azure e Microsoft Copilot, fornendo rinforzi indispensabili agli strumenti nativi dei clienti:
- Rileva gli aggressori che abusano di Azure Cloud
- Identifica gli attacchi reali in tempo reale collegando i vari elementi di Azure IaaS, Active Directory, Microsoft 365, Copilot e Microsoft Entra ID in un unico pannello di controllo.
- Blocca le violazioni di Azure, consentendo ai team di sicurezza di 1) identificare le lacune di sicurezza per Azure Cloud, 2) accedere facilmente ai registri delle attività e delle risorse Azure arricchiti e pertinenti e 3) intraprendere azioni decisive per contenere rapidamente gli account Microsoft Entra ID coinvolti in un attacco.
Gruppi dinamici
I gruppi sono stati ampliati per supportare l'adesione dinamica attraverso la definizione di un'espressione regolare (RegEx) che descrive i nomi dei membri da includere. Ciò consente un enorme risparmio di sforzi operativi nella gestione dei gruppi per la selezione o la valutazione. L'appartenenza al gruppo viene valutata in fase di esecuzione, per garantire che le nuove entità siano classificate correttamente senza alcuno sforzo aggiuntivo da parte vostra. Ciò si applica ai gruppi per host o account.
Data:
Novembre 2024
Rilascio:
2024.11
RUX: Fornitura SaaS
Query salvate per indagini avanzate
Ottimizzazione del processo di gestione delle query nell'esperienza di indagine avanzata di Respond UX grazie alla possibilità di salvare e condividere le query.
Gli analisti potranno creare, salvare, aggiornare ed eliminare le query in modo semplice, riducendo le ripetizioni e favorendo il riutilizzo. Gli analisti potranno anche condividere le query salvate con altri analisti, favorendo la collaborazione e la condivisione delle conoscenze all'interno dei team.
Data:
Ottobre 2024
Rilascio:
2024.10
RUX: Fornitura SaaS
La regione Svizzera è abilitata
Ora supportiamo le implementazioni di Respond UX in Svizzera. Ciò consente ai clienti svizzeri di ospitare i propri dati all'interno dei propri confini, se necessario. Questa nuova regione supporta tutti i prodotti Vectra.
I PCAP selettivi sono abilitati per i clienti della rete Respond UX.
Con questa versione, ora supportiamo completamente i PCAP selettivi per i nostri clienti della rete Respond UX. Questa funzione consente di sfruttare l'impronta del sensore Vectra per eseguire una cattura di pacchetti personalizzata in remoto, senza dover accedere all'infrastruttura locale.
Data:
Settembre 2024
Rilascio:
2024.09
RUX: Fornitura SaaS
Vectra Match Set di regole curato
Con questa versione, Vectra ha introdotto un link scaricabile che consente agli utenti di recuperare il set di regole curato per Vectra Match. Un nuovo link apparirà nell'interfaccia utente nella Match Vectra Match per i contenuti aggiornati quotidianamente, nonché utilizzabile tramite API. Per ulteriori dettagli, consultare Vectra Match Ruleset.
Data:
Luglio 2024
Rilascio:
2024.07
RUX: Fornitura SaaS
Copilot per M365 Dashboard delle minacce
Si tratta di una nuova dashboard in Respond UX per M365 incentrata sull'utilizzo di Copilot a livello aziendale. Utilizza questa dashboard per comprendere l'utilizzo di Copilot all'interno della tua organizzazione e quali file vengono consultati da Copilot.
Endpoint Integration Health aggiunti all'API V3
Nuovo endpoint API endpoint V3 Respond UX per fornire visibilità su integrazioni quali EDR, AD, ecc., consentendo di monitorare queste integrazioni critiche nel tempo.
Data:
Giugno 2024
Rilascio:
2024.06
RUX: Fornitura SaaS
Vectra Match disponibile nelle indagini istantanee e avanzate
Con questa versione, Vectra Match supportato in Respond UX. Il supporto Respond UX offre tutto il supporto WebUI e API fornito in Quadrant UX e aggiunge il supporto Instant e Advanced Investigation per Match . Per ulteriori dettagli, consultare la GuidaMatch .
Gestione utenti aggiunta all'API V3
Nuovo endpoint API endpoint V3 Respond UX per gestire gli utenti standalone all'interno del tenant Respond UX. Utilizza questa API per provisionare o deprovisionare automaticamente gli utenti dai tuoi playbook di onboarding o offboarding.
Data:
Maggio 2024
Rilascio:
2024.05
RUX: Fornitura SaaS
Blocco automatico dell'account AzureAD
Il blocco automatico dell'account AzureAD è progettato per fornire agli utenti Vectra meccanismi di difesa proattivi contro le minacce. Abilitando questa funzione, è ora possibile configurare due impostazioni fondamentali: Punteggio di urgenza e Importanza dell'entità. Questo approccio a doppia configurazione garantisce che, quando un'entità supera le soglie predefinite di Punteggio di urgenza e Importanza, entri automaticamente in uno stato di blocco per un periodo di tempo configurato dall'utente. Questo periodo consente un'indagine approfondita, garantendo che le potenziali minacce vengano investigate e affrontate in modo efficace.
Data:
Aprile 2024
Rilascio:
2024.04
RUX: Fornitura SaaS
Pannello di controllo delle minacce alla rete
Rilascio iniziale di una nuova dashboard Threat Surface per i nostri clienti della rete Respond UX. Questa dashboard rivela una grande quantità di informazioni sul vostro ambiente ed espone le vulnerabilità e i problemi di conformità. Sfruttate questa dashboard per esplorare l'uso di protocolli legacy e deprecati all'interno del vostro ambiente e garantire la conformità con le politiche stabilite per aree quali SMBv1.
Detect per AWS – Supporto per S3 copyObject nei log CloudTrail
Per impostazione predefinita, CloudTrail popola i bucket S3 con eventi putObject. Al momento dell'acquisizione, Vectra scartava gli eventi popolati con il comando copyObject. Con questa modifica, Vectra acquisisce gli eventi creati utilizzando copyObject o putObject.
Consolidamento del blocco di AzureAD e AD
Per i clienti che hanno la possibilità di bloccare sia gli account AzureAD che quelli AD (clienti con rete e Detect for AzureAD), abbiamo armonizzato l'esperienza per offrire un'esperienza complessiva migliore, integrando queste due diverse funzionalità e consentendo una maggiore visibilità e selettività per l'azione che si desidera eseguire. È possibile scegliere di bloccare Azure AD o AD, o entrambi, tutto dalla stessa esperienza.
Data:
Marzo 2024
Rilascio:
2024.03
RUX: Fornitura SaaS
Blocco automatico dell'account AD
Il blocco automatico dell'account AD è progettato per fornire agli utenti Vectra meccanismi di difesa proattivi contro le minacce. Abilitando questa funzione, è ora possibile configurare due impostazioni fondamentali: Punteggio di urgenza e Importanza dell'entità. Questo approccio a doppia configurazione garantisce che, quando un'entità supera le soglie predefinite di Punteggio di urgenza e Importanza, entri automaticamente in uno stato di blocco per un periodo di tempo configurato dall'utente. Questo periodo consente un'indagine approfondita, garantendo che le potenziali minacce vengano investigate e affrontate in modo efficace.
Miglioramenti alla gestione degli utenti
Questo miglioramento offre agli amministratori di Respond UX l'aspetto familiare dell'interfaccia di gestione utenti offerta dalla nostra piattaforma Quadrant UX. Gli amministratori possono ora gestire facilmente gli utenti e i loro ruoli, garantendo la massima accuratezza durante il provisioning degli utenti e il controllo degli accessi al sistema.
Accesso sospetto ad Azure AD da parte del Cloud
Vectra ha introdotto la possibilità di rilevare gli aggressori che compromettono un'identità e vi accedono da un cloud pubblico, come Amazon, Azure o GCP, per tentare di eludere il rilevamento e nascondere la loro vera posizione. Il rilevamento utilizza l'apprendimento automatico per identificare se un utente accede normalmente al proprio account dal cloud pubblico. Gli avvisi di Bening possono attivarsi quando un utente utilizza un'applicazione che passa attraverso un cloud pubblico cloud macchine virtuali cloud . Questo nuovo avviso darà la priorità a un account quando si verifica con altri avvisi in modo simile all'avviso di accesso sospetto di Azure AD.